1. Background
1.1 About TibCERT
The Tibetan Computer Emergency Readiness Team (TibCERT) is a formal, coalition-based structure for reducing and mitigating online threats in the Tibetan community, expanding Tibetans’ technical research capacity on threats in the diaspora, surveillance, and censorship inside Tibet, and ultimately ensuring greater online freedom and security for Tibetan society as a whole.
1.2 Purpose
The purpose of this TibCERT quarterly bulletin is to share updates about TibCERT and offer advice on digital threats observed in the community. We also aim to help Tibetans in the diaspora stay safe physically, emotionally, and digitally during the COVID-19 pandemic, as well as provide resources and awareness on issues surrounding the global pandemic.
1.3 TibCERT Updates
Since the national lockdown in India has lifted, we have resumed giving trainings and working with TibCERT members to create and implement digital security policies. However, since the number of positive COVID-19 cases keeps rising, our Digital Security Ambassadors (DSAs) are providing virtual support whenever possible and taking the utmost precautions when working with stakeholders in person. As the percentage of people using computers and smartphones has increased, so has the cybersecurity risks for users. Unfortunately, some members of TibCERT have fallen victim to cyberattacks. However, our team has responded to each incident and successfully secured our stakeholders.
1.4 Summary
The fifth edition of the TibCERT quarterly bulletin features:
1.4.1 Worldwide Developers Against Apple Censorship Conference 2020
On June 23rd, 2020, Tibet Action Institute hosted a day-long event: the Worldwide Developers Against Apple Censorship Conference (WWDAACC). We hosted three live, online panels with leading human rights and corporate accountability activists, researchers, journalists, and technology experts from around the globe. Discussions included the history and current status of censorship in China and Chinese-controlled regions like Tibet, the impacts on freedom of expression and access to information of Apple’s ongoing app removals from the Chinese App Store, and the effects for both iOS users living behind The Great Firewall as well as developers working to publish their apps.
In addition to the panels, a live coalition concert of artists from impacted communities was held, as well as two private hackathons to discuss questions surrounding iOS data localization and App Store censorship. Participants engaged in various research questions and planned future projects for continued exploration.
Just this month, the continuous coalition pressure on Apple from organizations like Tibet Action Institute, International Tibet Network, Students for a Free Tibet, World Uyghur Congress, GreatFire, and SumOfUs has achieved a landmark campaign victory. For the very first time, Apple has developed and issued a human rights policy, including the company’s commitment to freedom of information and expression as human rights.
1.4.2 App Bans in India and the US
Since the June 2020 Indo-China (Tibet) border clash between India and China, India has banned more than 200 Chinese apps, including popular apps like PUBG, WeChat, and TikTok. The US government has also made moves to ban WeChat and TikTok through its trade war with China.
1.4.3 Targeted Attacks Against Exile Communities
Targeted email attacks have risen once again in the Tibetan community, with Tibetan media, civil society organizations (CSOs), and TibCERT members under fire. These attacks are using fake email IDs to send malicious emails to their targets. As demonstrated by some similar indicators of compromise (IOCs), the attacks appear to be coming from the same attack group seen in 2019. At that time, one of our TibCERT stakeholder’s office systems was compromised by a watering hole attack (reported on by Kaspersky in April 2020). Our team has responded to all the incidents successfully and solutions for such attacks are detailed below.
1.4.4 Earth Empusa Threat Group Distributing Android “ActionSpy” Spyware to Target Minority Group in Tibet and Turkey
A report from Trend Micro shows that a malware called ActionSpy was used to target minority groups in Tibet, East Turkestan (Uyghurs), Turkey, and Taiwan. This malware is for Android devices and users are tricked into downloading an app from a phishing website. Once the malware is installed, it can steal all the information on the users’ device and send it to the attack group.
1.4.5 Digital Security Updates:
- There is a saying, “Those who rule data will rule the entire world.” Now that new 5G technology innovations are being created by state-backed companies (e.g., corporations like Huawei with a close relationship with the Chinese government), the newer generation of 5G can mean the compromise of one’s data and privacy.
- On the 30th of June, 2020, China enacted a sweeping new national law for Hong Kong. Before now, Hong Kong maintained certain freedoms with regard to the Chinese government (e.g., freedom of speech and press). However, with the passage of the new security law, Hongkongers are now in a state of fear. Authorities can crackdown on anything perceived as a protest—including speech—which inevitably contributes to higher levels of self-censorship. In addition, foreign companies are drawing out of the country and governments are currently recalibrating their relationships with Hong Kong.
- In this time of fast and accessible internet, China is using online disinformation campaigns to spread fake news and divide people. Below, we discuss cases where Beijing has spread fake news, as well as TibCERT strategies to avoid being a victim.
- Australian Prime Minister Scott Morrison spoke about state-backed cyberattacks on Australia which are targeting all levels of institutions, government offices, and organizations. Although he didn’t mention where these attacks are coming from, experts conclude that only China, Russia, Iran, and North Korea have the capability and possible intent to orchestrate such attacks, with cybersecurity experts long linking previous attacks to China.
2. Worldwide Developers Against Apple Censorship Conference 2020
Apple is one of the leading and most trusted tech brands in the world, with the company formally stating that “Privacy is a fundamental human right.” However, in reality, Apple has been complicit with the government of China’s censorship and surveillance demands, enabling crackdowns by Chinese authorities through its data relocation to mainland China and its removal of privacy apps from China’s App Store.
At the request of the Chinese government (and sometimes proactively), Apple has removed over 3000 apps from China’s App Store, including 1000+ virtual private networks (VPNs). In October 2019, the company removed “HKmap.live” from the App Store (globally) which is a mapping app used by Hong Kong pro-democracy activists to keep people safe. In March 2020, Apple also removed “Boom the Encryption Keyboard,” app netizens in China were using to circumvent censorship and share information about the coronavirus epidemic. Such examples demonstrate Apple’s compliance with the government of China’s censorship and surveillance, allowing Chinese authorities to violate people’s privacy, access to information, and free expression.
On 22nd June 2020, Apple hosted an online version of its famed Worldwide Developers Conference. Simultaneously, Tibet Action Institute hosted the first-ever Worldwide Developers Against Apple Censorship Conference (WWDAACC). The one-day program included leading human rights and corporate accountability activists, researchers, journalists, and technology experts from around the globe. Panelists included Tibetans, Uyghur, and Hongkonger representatives of communities affected by Apple’s actions, as well as speakers from the Citizen Lab, SumOfUs, Human Rights Watch, and GreatFire. The three virtual panel discussions included discussions on app censorship in Apple’s Chinese App Store and the effects for both iOS users living behind the Great Firewall, as well as developers working to publish their apps. In addition, a group of artists representing communities impacted by Apple censorship came together in a pre-event concert, performing traditional and contemporary music and discussing the impacts of Apple’s compliance with repressive demands by Chinese authorities.
The WWDAACC’s first panel was entitled Censorship in China & China-Controlled Regions: Then And Now. With Tibet Action’s Director Lhadon Tethong moderating, this panel included a diverse group of China researchers, academics, journalists, and technology experts with decades of collective experience in studying the government of China’s censorship regime. They discussed the history and impacts of censorship as well as contemporary implications of corporations and platforms that enable China’s efforts to change global norms around freedom of expression, including TikTok, Apple, and WeChat.
An important highlight of this session was a discussion on TikTok’s export of Chinese censorship to a global audience as outlined by Sam Biddle in his article in the Intercept. Given TikTok’s ownership by the Chinese company ByteDance, Biddle described the app’s censorship of political content deemed not in line with the Chinese government, such as users speaking in a way that harms “national honor” or talking about state institutions like the police. In addition, Biddle described the “invisible censorship of TikTok” and the content moderation team’s suppression of users based on a set of guidelines like “abnormal body shape,” “ugly facial looks,” “too many wrinkles,” or seen in “slums, rural fields” and “dilapidated housing.” While not outright blocking the videos, this practice makes sure the content is not seen and is a recent example of how supression of free speech by China’s authoritarian system has begun dangerously reaching across borders.
The second panel discussion was called Freedom of Expression & Apple: The Double Standard for China, Tibet, East Turkestan, and Hong Kong. In a recent letter to Apple employees, CEO Tim Cook said, “With every breath we take, we must commit to being that change and to creating a better, more just world for everyone.” But in reality, “everyone” does not actually mean everyone, especially if it means standing up to the Chinese government. In fact, there is a very deep and disturbing double standard when it comes to iOS users in the regions under Chinese government rule and panelists discussed the selectivity with which Apple chooses to resist government demands. For example, Apple refused to cooperate when the Federal Bureau of Investigations in the US wanted to access a suspect’s iPhone, stating the company could not comply due to issues of user privacy. Yet with the Chinese government, Apple routinely gives in to requests for the removal of apps authorities do not like (e.g., VPNs), leaving iOS users at great risk of surveillance. This is especially true since Apple’s 2017 transfer of data storage to mainland China for users under Chinese rule, allowing easy access for authorities to the data of those iOS users.
As one of the largest and most powerful tech companies in the world, Apple’s complicity with the government of China’s demands to censor certain apps has impacted the lives of millions of people, including Tibetans, Uyghurs, Chinese people, and Hongkongers—communities that were all represented on the panel. Panelists also discussed Apple’s responsibility to uphold its commitments to privacy and freedom of expression, especially for people living under authoritarian control who need access to privacy-securing technologies. The discussion touched on cases of people arrested while exercising their right to free expression, for example, simply stating opinions on the importance of Tibetan language and the poor state of Tibetan language preservation under Chinese law. In addition, panelists recounted a major shareholder vote in February 2020 (initiated and supported by several of the panelists) that would require Apple to report to shareholders on its freedom of expression policy (which it did not yet have) and to have more transparency on app removals. While not yet an enforceable mandate, the huge 40.6% approval showed a major appetite from shareholders for Apple to be more accountable, which panelists agreed they would follow up on and continue pressuring Apple to stand up to the Chinese government.
The third and final panel discussion was titled Publishing iOS Apps When Censored, bringing together technology experts and freedom of expression advocates from Tibet Action Institute, Guardian Project, GreatFire, and developers of Tibetan apps and the HKmap.live app (an app that was pulled globally from Apple’s App Store during the recent uprising in Hong Kong, triggering international media coverage and a strong letter to Apple from a bipartisan group of US Congress members). Panelists underscored the fact that Apple bans on iOS apps in China’s App Store market have major implications for human rights and access to information. They discussed the notion that code is free speech and recounted their experiences trying to publish apps in the App Store, at times being removed for simply being in Tibetan language. In fact, in a research collaboration between TibCERT and GreatFire, it was discovered that 29 Tibetan apps have been banned from Apple’s App Store with no clear explanation or documentation on what grounds the apps were removed. In fact, Apple’s transparency report routinely indicates that app removals are only for illegal content, citing “illegal gambling or pornography,” when in actuality, many apps are VPNs, Tibetan apps, and others that the Chinese government simply deems unacceptable. In such cases, the panelists also discussed ideas for publishing apps when censored by app stores and the Chinese government.
Other than the online panel discussions, Tibet Action also held two hackathons/private sessions with around 15 participants in each, including researchers, developers, activists, and digital security/technology experts. A hackathon is a tool used in tech circles to explore questions one does not yet know the answer to but wants to figure out, in this case, focusing on Apple’s operations in China and Tibet. The first session centered on iCloud since in 2018, Apple transferred iCloud operations to Guizhou-Cloud Big Data (GCBD) in China, along with iCloud encryption keys. The discussion focused on how iCloud censorship works in terms of surveillance and censorship in Tibet and China. Given Apple’s removal of thousands of apps from China’s App Store, the next session focused on Apple’s App Store censorship. The participants posed major questions around talk/chat Apps that are censored in China’s App store (e.g., Viber, Line, Wire, and many others), while at the same time, others remain available (e.g., Signal). In the coming months, TibCERT will work with other organizations and hackathon participants on ideas that came up during the sessions. For example, we will work on advocacy for more transparency by researching and analyzing Apple’s transparency data since 2016, as well as looking more deeply into the bases for which Apple removes apps from the App Store. In addition, we will work to better understand how end-to-end encrypted apps like iMessage and Signal work in China and Tibet. We are excited about these continued collaborations and the potential benefits they can contribute to building more freedom of expression and transparency for iOS users of China’s App Store.
Overall, the WWDAACC was an inspiring gathering, bringing together established partners in the #StopAppleCensorship coalition campaign along with new partners and ideas to help challenge Apple’s complicity with Beijing’s censorship and efforts to change global norms around freedom of expression.
Just this month, in a major campaign success for the coalition, Apple has for the very first time established a formal human rights policy, including a public acknowledgement of freedom of information and expression as human rights (a specific campaign goal). This was due to the hard work of organizations like Tibet Action Institute, Students for a Free Tibet, International Tibet Network, World Uyghur Congress, SumOfUs, and more in strategically pressuring Apple. While this is a critical first step, the coalition will continue working to press Apple on implementation and oversight, so the policy does not remain only on paper but actually positively impacts the lives of communities living under China’s rule, including Tibetans. This will include dialogue directly with Apple executives, conversations of which are already underway.
3. Apps Banned in India and the US
3.1 Overview of the App Ban
It is important to recognize that accessing the internet on your device is a way that the privacy and security of your personal and professional life can be breached through surveillance and/or cyberattack. The applications you trust to store, send, and receive your personal data may not be trustworthy. For example, some applications can use their servers to watch, manipulate, and misuse your personal data for the benefit of others. Currently, several federal governments are addressing the issue of user privacy and security impacted by particular social networking applications, treating these issues as a top priority for maintaining a digitally secure nation.
In one example, as of June 2020, India has banned a total of 224 Chinese Apps (59 in the first round, 47 more in a 2nd round, and 118 more most recently in September). The bans have come due to data privacy concerns, fundamentally sparked by the border disputes between India and China in June of this year. The Indian government stated that these apps were banned under Section 69A of the Information Technology Act, 2000 because “they are engaged in activities which are prejudicial to sovereignty and integrity of India, defense of India, the security of the state and public order.” Since 2017, the government has received reports from intelligence agencies naming certain apps as spyware, indicating “the misuse of some mobile apps for stealing and surreptitiously transmitting users’ data in an unauthorized manner to servers located outside India.” TikTok, WeChat, and PUBG mobile are the most popular Chinese apps which are on the list of apps so far banned by the Indian government. Even before this year’s official ban of Chinese apps in India, in 2017, the Ministry of Defence ordered the Indian armed forces officers and all security personnel to uninstall over 42 Chinese apps, including Xiaomi’s Mi Store ad Mi Community. This shows that the Indian government has held concerns about a threat to the national privacy and security of India years before an official ban was imposed.
Similarly, on August 7th of this year, US President Donald Trump signed executive orders to ban the popular Chinese apps WeChat and TikTok, stating that these apps are a threat to national security, foreign policy, and the economy of the United States. The orders are based on the allegation that an unprecedented amount of user data collected by the Chinese government gives authorities access to the personal and proprietary information of Americans, thus potentially allowing China to track federal employees and contractors, build dossiers of personal information for blackmail, and conduct corporate espionage. In order to avoid being banned in the country, Trump set a September 15th deadline for TikTok to find a US buyer (to remove any trace of Chinese server influence on the app ). In the beginning, Microsoft and Walmart were mentioned as collectively pushing forward talks to acquire the app. However, as the deadline approached, Oracle won the bidding for the US operations of TikTok. This is the latest in US government action against Chinese companies, firms, and institutions thought to be helping Beijing spy on its minority Uyghur population or because of ties to weapons of mass destruction and China’s military. The list of blacklists includes Huawei, some of China’s top artificial intelligence startups, and the video surveillance company Hikvision.
A ban of this multitude of insecure Chinese apps by India and the United States creates an opportunity for all the Tibetans living in India and the US to switch to better and secure apps since using Chinese apps like WeChat creates a high level of privacy concerns for Tibetans in the diaspora.
3.2 Alternatives by TibCERT
Given that WeChat is the most frequently used app among Tibetans living in India for communication with their loved ones inside Tibet and China, it’s important to know about alternatives that are practical as well as secure in user data privacy. Applications such as WhatsApp, Signal, and Zom are suggested as alternatives for WeChat due to their high encryption protocols such as “end-to-end encryption.” In order to help share information, TibCERT has posted on our blog information on 59 of the Chinese apps banned by India, their descriptions, and suggestions for their respective alternatives. https://blog.tibcert.org/59-banned-Apps /
3.3 Checking Apps and Identifying Which is Suitable for Your Data Security
With the undercurrent of governments banning these Chinese apps, it is a perfect time for us as users to differentiate between secure and insecure applications. Apps that consist of proper data privacy policies should be given priority regardless of their inefficiency compared to less trustworthy, Chinese alternatives. There are major factors we need to consider to figure out whether an app is trustworthy or suitable for your data security before downloading it and using it. These factors are as follows:
3.3.1 Location of Data Center (Outside China)
The most crucial factor for any Tibetan choice of an application is how it collects user data and its security. The location of the application server plays an important role as the servers follow the specific laws associated with the countries where they are located. Under China’s draconian cybersecurity law passed in 2017, app servers located in China provide user data if and when Chinese authorities make a demand. Therefore, this data can be used for state surveillance and censorship whenever desired. The Great Firewall of China is also a factor that helps the Chinese government enhance its online censorship capabilities, blocking information deemed sensitive or out of alignment with the government’s narrative. Thus for your data privacy, it’s important to research and ensure that the app you want to download has its servers outside of China, or at least keep a separate phone just for such apps so that the rest of your data is not vulnerable to surveillance and attack. One can usually go through the “privacy policy” of apps available on Google’s Play Store or Apple’s App Store. You can check the policy to learn about its server location, what data it collects, and how the app uses your data.
3.3.2 Creator, Founder, and Developer
All applications in the Play Store or the App Store consist of a creator, founder, and a developer. It is important to know the background and origin of an app, specifically tracing whether it has anything to do with China given the country’s cybersecurity laws. Any app which consists of a Chinese creator, founder, or developer must be researched thoroughly. We don’t claim that every Chinese app is malicious or that it misuses user data, but we believe that there is a potential risk of trusting such apps. It is not safe to provide or exchange your personal data using some apps as a means of communication (or on social media), especially when an app’s creator, founder, and developer have some connection to the Chinese government. Before installing an app, one can easily check the developer in the app’s description as listed in the Google Play Store or Apple’s App Store.
3.3.3 Encryption Type
Users of apps for online communication and file sharing in the form of text, audio, image, and video want to have their conversations secured and their privacy protected. It is important to know, therefore, about the encryption protocols used by these apps as it determines how data is traveling. An end-to-end encryption protocol is a must for any secure online communication. In such a protocol, the message is scrambled and encrypted from the time it leaves the sender’s device to the time it arrives at the recipient’s, with only the recipient’s device possessing the digital “key” necessary to decrypt the message. In such a method of communication, even the application server cannot decrypt the message to watch the conversations or censor any data. Applications such as WeChat and QQ do not use end-to-end encryption and instead use transport layer encryption, which means a plain text message gets encrypted at the sender’s end and decrypted at the server. In this type of communication, the server can use your personal data for surveillance and censorship. Before downloading any online messaging app, it is important to check if it uses end-to-end encryption in order to secure your data and conversations. Applications such as Signal, Element, and Zom are some examples of apps which use end-to-end encryption methods and are highly secured so that their own servers cannot decrypt the conversations you are having in the app.
3.3.4 Check History
Checking the background history of the applications you want to install is very important. Some apps have a history of major surveillance and censorship of users’ data and the content that they post online. For example, WeChat has a long history of surveilling and censoring texts, audios, pictures, and videos that are perceived to cause harm to the reputation and image of the ruling government where the user is registered (e.g., the Chinese Communis Party). Some Tibetans living inside Tibet have been imprisoned based on their WeChat conversations, including speaking about independence for Tibet and human rights violations by China. In another example, TikTok has a history where certain individuals posting content about the ongoing 2019-20 Hong Kong pro-democracy protests or who raised their voices against the ill-treatment of Uyghur Muslim minorities by the Chinese government were censored and had their TikTok accounts banned. According to an article in the Independent, a class action lawsuit in the US claims that TikTok comes with pre-installed surveillance software and that “TikTok also has surreptitiously taken user content, such as draft videos never intended for publication, without user knowledge or consent. In short, TikTok’s lighthearted fun comes at a heavy cost.” In addition, the lawsuit alleges that draft videos created by one of the plaintiffs were “sent to two servers in China owned by Chinese tech giants Tencent and Alibaba.”
In conclusion, before downloading any app, it is highly recommended to research the history of the app and its owner regarding their user privacy policy, human rights violations if any, and past activities of user data surveillance and censorship. Visit TibCERT’s website https://blog.tibcert.org/ for a detailed description of some popular yet controversial apps such as WeChat, TikTok, and Zoom.
4. Targeted Attacks Against Exile Communities
Since 2007, the Tibetan community has been the recipient of various targeted malware attacks originating from China that we believe are likely being committed by the Chinese government or at the behest of the Chinese Government. A report published by Proofpoint disclosed information on recent, targeted email attacks sent to members of the Tibetan community containing malicious attachments referencing COVID-19 information. The fake emails impersonated the World Health Organization (WHO) and included an RTF attachment of the WHO’s “critical preparedness, readiness, and response actions for COVID-19, Interim guidance.” This guidance was initially published by the WHO on March 7, 2020, while the weaponized attachment was delivered by threat actors on March 16, 2020. The attackers presented themselves as “DIIR INFO Secretary” using the email address “tseringkanyag@yahoo[.]com.” (see Figure 1 below). This fake email looks very authentic and, as a result, one might think it was actually from a legitimate sender at the WHO. Given the prolific nature and growing sophistication of such online attacks, it continues to be extremely important to follow the digital security guidelines we have detailed in the past, including “Think Before You Click” and “Detach From Attachments.”
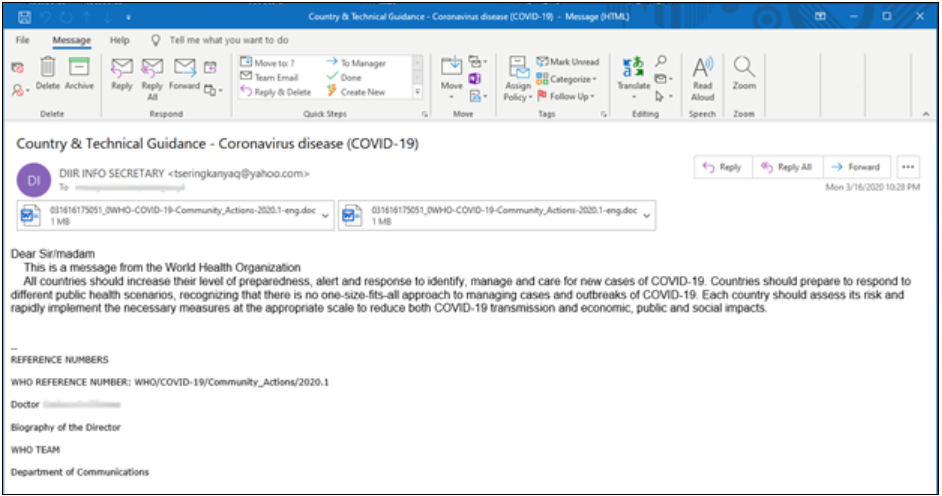 Figure 1: Malicious fake email from DIIR INFO SECRETARY on Country & Technical Guidance -Coronavirus disease (COVID-19)
Figure 1: Malicious fake email from DIIR INFO SECRETARY on Country & Technical Guidance -Coronavirus disease (COVID-19)
4.1 TWA and Delek Hospital Fake Emails (with TibCERT Solutions)
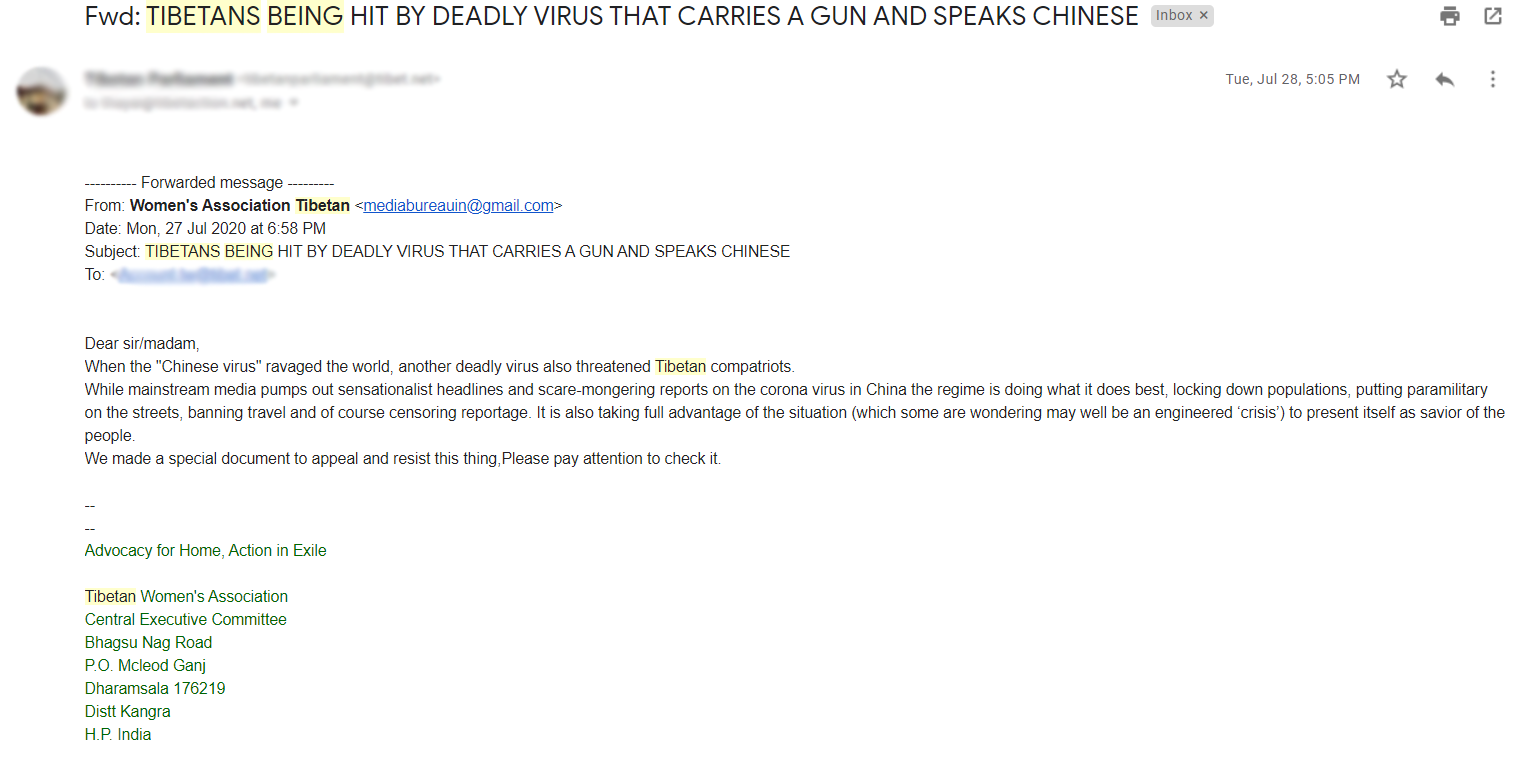 Figure 2: Email sent by mediabureauin@gmail[.]com impersonating TWA
Figure 2: Email sent by mediabureauin@gmail[.]com impersonating TWA
Amidst the pandemic, TiBCERT has also discovered similar targeted, themed emails that were sent to members of the Tibetan community. The above email (Figure 2) was sent to various Tibetan organizations and media groups on the 27th of June, 2020, originating from a fake Tibetan Women’s Association (TWA) email account with the address mediabureauin@gmail[.]com. This email contains a malicious PowerPoint (PPSX) attachment conspicuously named ”TIBETANS BEING HIT BY DEADLY VIRUS THAT CARRIES A GUN AND SPEAKS CHINESE.ppsx.” When the attachment is opened, a Sepulcher malware payload named “file.dll” is downloaded and saved as “credential.dll,” resulting in a C2 communication with the domain dalailamatrustindia.ddns[.]net.
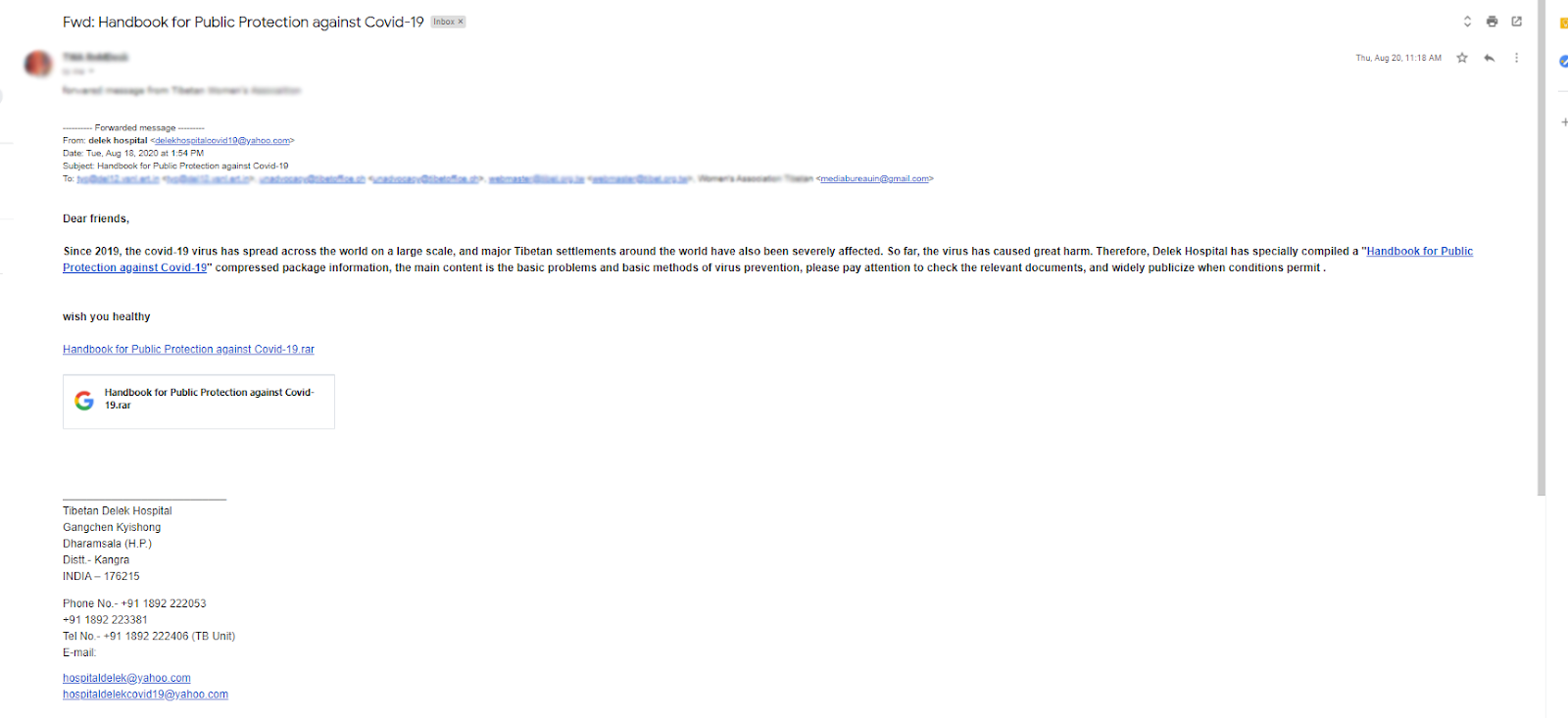 Figure 3: Fake email address pretending to be from Delek Hospital
Figure 3: Fake email address pretending to be from Delek Hospital
A similar email was sent from a fake Delek Hospital email account. Again, with the ongoing pandemic, it can be easy to open such an email claiming to have information on COVID-19, especially from a known organization. Taking advantage of the situation, this phishing email was sent to many media groups and Tibetan nongovernmental organizations with the subject line “Handbook for Public Protection Against Covid-19.” The email had a Zip file attached to it and the content could easily seem very genuine, underscoring the crucial need to make sure any links and attachments you open are from trusted, verified sources.
The analysis on this COVID-19 targeted themed attack was not possible as the malware was blocked by Google as malicious, however, we believe that this is part of the same campaign since the email id mediadureau.in@gmail[.]com, (as seen on all the emails reported in the Proofpoint report) can been seen in the cc: of all the targeted emails. This email address was also seen in a January 2019 targeted attack that utilized PPSX attachments to deliver ExileRAT malware.
TibCERT Incident Response
In response to the above incidents (of which TibCERT was aware of two of them), our Digital Security Ambassador guided the organizations whose names were used for fake emails to inform all the email receivers not to open the email and especially not to click on any links or attachments in the email. Further, we checked the details of the email and analyzed them as thoroughly as possible. We also reached out to the civil society TibCERT members who we felt may have been targeted with these attacks and informed them about the attacks and solutions.
As seen in earlier attacks, the Tibetan community tends to be targeted as a community and when one organization is targeted, others also tend to be targeted. As such, it is paramount to share information with TibCERT as it allows us to alert others as well about dangerous emails. The fact that we only heard about the “tseringkanyag@yahoo[.]com” fake email through the Proofpoint report highlights the need for the community to do more threat sharing so that we can better protect each other.
As mentioned, with ongoing threats it remains extremely important to continue utilizing best practices for avoiding attacks. First, you should always “Think Before You Click.” Whenever you receive an email from an unfamiliar sender, it is crucial to verify the email address and make sure it is someone you can trust. Also, always beware of links. Before clicking a link, you can verify it by copying the link into https://virustotal.com and scanning it for potential malware.
One more important best practice is to “Detach from Attachments.” An attachment such as a Word Document, PDF file, or any type of file can be weaponized with malicious software which can be used to infect your computer when opened. The best alternate approach for sharing information is to use Google Drive instead of attachments. Google has up to 15 GB of free storage for each account, and content can be uploaded into Google Drive and shared within or outside your organization. You can also refer to our Knowledge Base website https://learn.tibcert.org/ to help better understand other best practices.
4.2 Watering Hole Attack on TibCERT Stakeholder (with Solutions)
In TibCERT’s last Bulletin (Issue 4), we explained that a “watering hole attack” is a security exploit in which the attacker seeks to compromise a specific group of end-users (e.g., the Tibetan community) by infecting websites that members of the group are known to visit. In March, one of our members fell victim to such an attack. The attack occurred through a pop-up appearing on the screen stating, “Please install the latest Flash Player.” When clicked on by one of the staff members, the malware spread amongst the computers of other employees connected to the same network.
TibCERT Incident Response and Solutions
In June, we found out about the infection and our team immediately took the necessary action by going to the infected members’s office and using tools to scan the organization’s computers. We found that almost all of the computers were infected with the same type of malware. Our team removed the malware from those computers and saved it in a separate external drive for further analysis.
In order to avoid becoming a victim of such attacks, it is critical that every staff member is aware of basic digital security knowledge, since one small mistake can lead to a huge loss in one’s organization. Once again, a pivotal concept for avoiding such a scenario is to “Think Before You Click,” remembering it is important to be very careful of unknown links or pop-ups that appear without cause. If you suspect you have been the victim of an attack or receive any dubious emails, please reach out to TibCERT at support@tibcert.org for such cybersecurity-related issues. Also, to keep up with the best practices, please refer to https://tibetaction.net/digitalsecurity/onlinesecurity/.
4.3.1 About ActionSpy
The Earth Emphusa Group (also known as POISON CARP/Evil Eye) is a threat group distributing a new Android spyware named ActionSpy. During the first quarter of 2020, Trend Micro (a leader in the field of data defense and cybersecurity) detected new Android spyware targeting users in East Turkestan, Turkey, Tibetans in the diaspora, and more recently, Taiwanese users. While the group was previously known to implement watering hole attacks, this time a phishing attack was used to deliver the malware payload to the victims’ devices.
In a June report, Trend Micro stated, “The malware that infects the mobile devices are found to be associated with a sequence of iOS Earth Empusa Threat Group Distributing Android ‘ActionSpy’ Spyware to Target Minority Group in Tibet and Turkey exploit chain attacks in the wild since 2016. In April 2020, we noticed a phishing page disguised as a download page of an Android video application that is popular in Tibet. The phishing page, which appears to have been copied from a third-party web store, may have been created by Earth Empusa. This is based on the fact that one of the malicious scripts injected on the page was hosted on a domain belonging to the group. Upon checking the Android application downloaded from the page, we found ActionSpy.” Later in April, Trend Micro found another phishing page injected with scripts to load ScanBox and BeEF frameworks. This page was also running on a domain reportedly belonging to Earth Empura.
4.3.2 How It Works/Mechanism
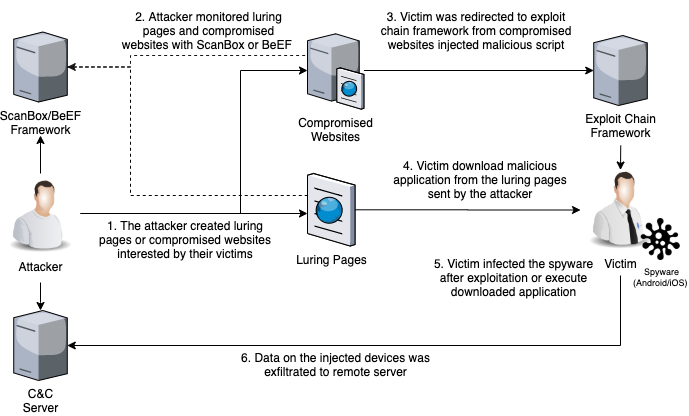 Figure 4: The Earth Empusa attack chain as seen in Trend Micro report
Figure 4: The Earth Empusa attack chain as seen in Trend Micro report
The Trend Micro report highlighted that the attack was impersonating a popular Tibetan video app, though detailed information was not shared. In addition, the malware is said to use the help of VirtualApp to impersonate Ekran—a legitimate Uyghur video app—generating the same appearance and functionality as the original app. The cherry on top is that the malware is protected by Bangcle, a mobile application security provider. Bangcle encrypts apps to prevent them from being hacked, reversed, repacked, and run-time injected, helping them evade static analysis and detection.
ActionSpy collects basic device information, including IMEI, phone number, manufacturer, battery status, etc. It then sends it to the C&C server, encrypted with RSA and communicated via HTTP connection every 30 seconds.
| Module Name | Description |
|---|---|
| location | Get device location latitude and longitude |
| Geo | Get geographic area like province, city, district, street address |
| contacts | Get contact info |
| calling | Get call logs |
| SMS | Get SMS messages |
| Net trace | Get browser bookmarks |
| software | Get installed APP info |
| process | Get running processes info |
| wifi connect | Make device connect to a specific Wi-Fi hotspot |
| wifi disconnect | Make the device disconnect to Wi-Fi |
| wifi list | Get all available Wi-Fi hotspots info |
| dir | Collect specific types of file list on SDCard, like txt, jpg, mp4, doc, xls. |
| file | Upload files from device to C&C server |
| voice | Record the environment |
| camera | Take photos with camera |
| screen | Take screenshot |
| Get the structure of the WeChat directory | |
| wxfile | Get files that received or sent from WeChat |
| wxrecord | Get chat logs of WeChat, QQ, WhatsApp, and Viber |
Table 1: Modules supported by ActionSpy from Trend Micro report As mentioned above, the threat group is targeting minority groups like Tibetans, Uyghurs, Taiwanese, and Turkish people, installing spyware to steal information that is sent to the attack group. The malware also exploits accessibility through which the attacker can acquire a user’s official and private information such as nicknames, chat contents, and chat time from WeChat, WhatsApp, Viber, and any other installed messaging apps. Given the specific groups targeted, it can be assumed the attacks are politically motivated. However, as of now, there is no clear indication of what Earth Empusa does with the data collected using ActionSpy.
5. Digital Security Updates:
5.1.1 5G Real-time Impact on Surveillance and Censorship
5G is the fifth generation of wireless network technology which is said to be faster than the current 4G LTE network with an average download speed of 150Mbps – 200Mbps. It will be a massive boost to the Internet of Things (IoT) and related new products and innovations.
When we talk about 5G, people commonly think about the increase in speed. However, there are also a lot of advantages other than speed. 5G has greater bandwidth which means more devices can be connected to the network. It will also pave the way for more futuristic projects like self-driving cars and artificial intelligence advancements. Since it reduces the latency to virtually zero, cell phones have a better connection for making requests and getting responses from the server. It will also enable cloud computing services like Amazon Web Services (AWS) and Microsoft Azure to operate faster and easier.
5.1.2 Impact of 5G on Cybersecurity
Huawei (the largest provider of hardware equipment around the world) recently came under scrutiny for allegations of stolen intellectual property and its relationship with the Chinese government. Although the company has completely denied the allegations, the question remains whether Huawei can go against strict policies in China’s cyberlaw which compels companies to share their user data with the government. Given China’s track record of cyberattacks, there is a worrisome risk of Huawei’s technology being used for state espionage.
Due to such risks, many countries are considering cutting ties with Huawei. While wealthy countries like the US and Australia can afford to do so, some countries are already deeply rooted in Huawei for their current infrastructure. If they end the relationship with Huawei, it will be a huge endeavor to reinstall a new network infrastructure, costing a fortune to the country and potentially delaying the adoption of 5G technology.
In a recently released report from the Government Communications Headquarters (GCHQ), the cyber-intelligence agency of the United Kingdom (UK), it states that Huawei has failed to adequately resolve security flaws in the equipment used by UK telecom networks. As a result, GCHQ no longer considers Huawei technology safe and as such, there is a strong concern that Huawei technology will be unable to resolve security flaws in their 5G technology deployment, presenting a number of security issues and vulnerabilities that can be exploited in the long run.
In general, 5G antennas have a shorter range than the previous 4G LTE ones, meaning 5G networks need more antennas to operate. As a result, many more routers will be needed for 5G operations, mostly handled through software such as SDN and NFV. Since the technology is new and less tested, it will be very difficult to close all the security vulnerabilities. Therefore, there is a huge possibility that a software vulnerability in some of a network’s antennas and routers could crumble the entire network. In addition, 5G technology is not just for phones. Important infrastructure areas such as hospitals, traffic lights, smart cars, and much more will be connected to one another via 5G networks. A breach could cause serious consequences to the devices connected to that network, impacting a cross section of society.
Furthermore, when a 5G device switches to 3G or 4G, it’s exposed to the vulnerabilities that haven’t been addressed in the previous generations’ protocol. When a dependable 5G signal isn’t available, the 5G networks will continue to be vulnerable to attacks such as spoofing, fraud, user impersonation, and denial-of-service to allow 4G or 3G connections (legacy technologies). Network operators will continue to rely on GPRS Tunneling Protocol (GTP), which, in of itself, has a number of well known fundamental flaws.
“One of the core flaws in GTP protocol is the fact that it does not validate the user’s physical location, making it possible for an attacker to spoof their traffic’s location, says Jimmy Jones, a cybersecurity expert at Positive Technologies.”
Finally, another 5G network flaw is that attackers can steal credentials or spoof user session data and a real phone number to impersonate other subscribers. This enables a huge number of connected devices, collectively known as the “internet of things” (IoT). Attackers can then use this to access network services to send requests to open up multiple data connections on a single access point in a denial-of-service attack that can paralyze networks.
5.1.3 Impact on Tibet and Tibetans
Currently, the benefits offered by 5G may pale in comparison to the threats posed by 5G technology, especially given that Tibetans are constantly under Chinese surveillance through highly sophisticated surveillance cameras using artificial intelligence. Now, with the help of 5G, the possibilities for surveilling Tibetans and other communities like Uyghurs are endless. The government of China will be able to collect data faster and can easily pin-point the location of communication far better than through 4G LTE, since there will be more network antennas and routers to triangulate a user’s cell location or IoT. As such, IoT devices will be increasing significantly once 5G is available in the market.
During the pandemic, while the whole world has been under lockdown amidst fear of COVID-19, the government of China has been busy building and expanding its surveillance network to strengthen and maintain control over people living under the CCP. For example, while most of China was under lockdown and Mount Everest was closed to climbers, Huawei and the state-owned network provider China Mobile teamed up to build the world’s highest 5G base station on Mount Everest, sitting at an altitude of 6,500 meters. While experts continue to warn about the security loopholes of 5G technology and its ability to increase surveillance and censorship, China has recently overtaken the United States in terms of the number of 5G network relays, making it potentially easier for the government to exploit the technology for its own gains.
Professional climber Conrad Anker (who has summited Everest three times since the late ‘80s) recently spoke about his fear that 5G will open up the world to Tibet through a flood of media on the internet that could give a false narrative. Tibetans have been living under the Chinese regime since 1950 and are already having trouble preserving the religion and culture as a result of the occupation. Like the rest of China, the internet will continue to be censored and the government will hide or alter the facts about the sovereignty of Tibet before 1950, a great concern for the Tibetan people.
For many places in the world, 5G has the potential to be a blessing of modern network technology that brings digital innovation and futuristic technology to new generations. However, the reality on the ground for the Tibet and Tibetan people will be the loss of what little privacy is left through China’s tightening of surveillance in order to restrict any sort of political challenge.
5.2 Impact of New National Security Law in Hong Kong
On June 30, 2020, Beijing announced a new national security law in Hong Kong. The new law was kept secret until it was enacted and only a handful of people saw the full text of the law before the announcement. In 1997, Hong Kong was handed back to China from British control with a so-called “one country, two systems” principle and governance through what was called the “Basic Law” which was supposed to protect some freedoms like freedom of assembly and speech, an independent judiciary, and some democratic rights. Under the same agreement, a national security law was enacted but it never happened because of its unpopularity. This new national security law, however, gives China full control of Hong Kong.
In the few months since the enactment of the new law, Hong Kong citizens are now filled with fear and uncertainty, because anything that is seen to instigate distrust against the Chinese government is punishable with up to life imprisonment. According to several lawyers, the law is so unclear and broadly defined that almost any action can be argued to be in violation and, as a result, many are turning to self-censorship or leaving Hong Kong in order to remain safe. Of particular concern is the fact that any interpretation of the law will come from mainland China not the local authorities, and if there is a conflict with any Hong Kong law, the Beijing law will be the standard used.
As a result, people have started censoring themselves, their social media posts, and erasing messaging app histories in fear that their online activity might be deemed offensive to the Chinese government. Journalists are busy removing their digital footprint, fearing their work might be judged as inciting secessionism. Books are being removed from libraries or under review and schools have been told to review course materials to ensure nothing is in violation. Shops have removed walls of Post-it Notes bearing pro-democracy messages in fear of the new law. As reported by TIME, slogans like “Liberate Hong Kong, the revolution of our times” have been outlawed.
The political landscape in Hong Kong is also being affected. For example, the youth political party Demosisto founded by activist Joshua Wong was disbanded on the same day the new national security law was introduced. Other upstart political organizations have relocated overseas because of the potential repercussions of the new national security law.
Hong Kong’s New National Security Law has also caused profound apprehension among nongovernmental organizations and news agencies, making some leave the city and, at times, leave sooner than expected. On July 14, for example, the New York Times announced it was relocating its Hong Kong-based digital news operation to South Korea due to visa problems and the city’s “new era under tightened Chinese rule.” In addition, the police force has been given new powers and can now regulate online content and intercept communications. This may compel companies to censor content as well as hand over private user data. In response to this, tech companies like Facebook, Google, and Twitter announced a pause on data requests until the companies can review the law and consult with international human rights experts.
The majority of US companies operating out of Hong Kong were increasingly concerned about the law being open to more than one interpretation, as shown in a survey by the American Chamber of Commerce. Yet among businesses in the financial sector, there has been a mixed reaction with some expecting this new law will have no effects or rather positive effects with the suspension of protests, which had hindered their operations.
With freedoms now taken away from people and companies, as well as the right of the Chinese government to make data requests and use that data against people, the enactment of the new law means the end of the one country, two systems principle and signals the beginning of the type of state of repression and surveillance for Hong Kong that has been established and developed in Tibet.
5.3 Chinese Disinformation Campaigns in US Elections
Times have changed drastically since the invention of the internet and the current generation of information has frequently changed to one of disinformation. Disinformation means knowingly and deliberately spreading false, misleading, or manipulated narratives or facts. Disinformation is at its core a form of propaganda, with various motivations behind its creation.
Disinformation is a common tool of espionage and is as destructive as it is divisive. For example, the Chinese government spread false information about COVID-19 and blamed the outbreak on the United States. When a country or group coordinates a plan to spread disinformation, it is referred to as a disinformation campaign.
Some instances of disinformation campaigns that China has been involved in:
- Countries all over the world have been concerned about Russian interference in the US elections. Unfortunately, though, Russia is not the only one. As stated in a US intelligence report, there are other expert players like Iran and China who studied what the Russians did in the 2016 election and are using similar tactics.
- Countries all over the world have been concerned about Russian interference in the US elections. Unfortunately, though, Russia is not the only one. As stated in a US intelligence report, there are other expert players like Iran and China who studied what the Russians did in the 2016 election and are using similar tactics.
- Countries all over the world have been concerned about Russian interference in the US elections. Unfortunately, though, Russia is not the only one. As stated in a US intelligence report, there are other expert players like Iran and China who studied what the Russians did in the 2016 election and are using similar tactics.
- Countries all over the world have been concerned about Russian interference in the US elections. Unfortunately, though, Russia is not the only one. As stated in a US intelligence report, there are other expert players like Iran and China who studied what the Russians did in the 2016 election and are using similar tactics.
With more than half the people in the world now having access to the internet, information is being shared and accessed widely and in different forms. However, it is clear that not all the information is true. Since China has a huge influence on many corporations and politicians, we should all be highly on guard against disinformation from China or any other source for that matter. It is critical to verify information before sharing with others in the Tibetan community. Here are some of the disinformation and misinformation examples in our community which have been verified as false and posted on our website at https://learn.tibcert.org/category/disinfo-misinfo/
5.4 Australia Hit by Massive Cyberattacks, China Suspected
On June 19th, Australian Prime Minister Scott Morrison announced state-based cyber attacks on various levels of Australian government and institutions. He declined to name the country responsible but assured it was no major data breach. He also said the announcement was aimed to raise awareness for the public and institutions in order to inspire improvement in their defense against cybercrime. He concluded by saying the “malicious” activity is happening all over the globe. Mr. Morrison did not specify any incidents but he did state, “This activity is targeting Australian organizations across a range of sectors, including all levels of government, industry, political organizations, education, health, essential service providers, and operators of other critical infrastructure.”
During the conference, Mr. Morrison said officials had identified the incidents as state-backed cyberattacks based on three points: the scale of the cyberattack, the nature of the targeting, and the methods used. However, Mr. Morrison refused to name any country as the culprit. Yet cyberintelligence experts have long suspected China of various cyber-attacks in Australia.
As we know, ongoing cyberattacks are happening in the Tibetan community as well, targeting various levels of exile-government, institutions, and civil society. We also know that protection against cyberattacks is not a one-day process. We have to improve our technical defenses every day. Within any organization or institution, every staff member is equally responsible for maintaining a high level of security, not just the head of the technical support team. Therefore, it is very important to improve digital security awareness of all employees through trainings and keeping everyone’s knowledge of digital security up to date.