1.Background
1.1 About TibCERT
The Tibetan Computer Emergency Readiness Team (TibCERT) is a formal, coalition-based structure for reducing and mitigating online threats in the Tibetan community, expanding Tibetans’ technical research capacity on threats in the diaspora, surveillance, and censorship inside Tibet, and ultimately ensuring greater online freedom and security for Tibetan society as a whole.
1.2 Purpose
The purpose of this TibCERT quarterly bulletin is to share updates about TibCERT and offer advice on digital threats observed in the community. As we enter the new year, it’s important to keep ourselves abreast of digital security “best practices,” ensuring that we can all build the capacity to protect against digital threats and keep ourselves and our communities safer online.
1.3 TibCERT Updates
The year 2020 will be marked in history as one of the hardest years ever seen, with countries locking down and often empty streets. For many, though, it has also brought us closer to our family and loved ones. However, with the new normal still continuing, unprecedented cybersecurity threats are emerging from around the globe. We have never relied on technology and the Internet more than now, whether staying connected with each other or for our work. However, with this greater reliance on technology also comes more risk of cyberattack and the spread of misinformation and disinformation. Therefore, more vigilance than ever before is required.
1.4 Summary
This issue of the bulletin features:
- Tibetans in the diaspora have been under the spotlight of Chinese socially engineered cyberattacks. To help mitigate these threats, TibCERT has successfully set up its first community-based Response Hub in Dharamsala. This hub will operate through the fundamentals of Learn, Share, Network, and Support. Through the establishment of multiple community-based Response hubs, TibCERT will be expanded through this network to support the community globally. These hubs will also be able to identify the issues that our community is facing, finding solutions, and supporting our networks.
- Targeted Attacks on the Tibetan community:
- This year’s Geneva Forum organized by the Central Tibetan Administration (CTA) was held virtually on Facebook. While there were only a total of around 100 people watching live at any given time, there were more than 50,000 comments. This was due to many fake accounts being used to disrupt the forum by spreading disinformation. It looks like all the fake accounts were run by a group of people, making it an organized campaign. According to a Tibet Policy Institute researcher, the syntax used in the Tibetan language comments was the same as one used by Tibetans living inside Tibet and clearly a campaign run by the 50 Cent Army.
- We have also noticed ransomware attacks in our community in which the attacker encrypts the server, making it impossible to access the website unless a ransom is paid. In one instance, the website of an institute was compromised. Another case was found in Mundgod where a drive folder of a Tibetan monk’s computer was encrypted.
- For more than 10 years, our community has been targeted with cyberattacks. While in recent years, the numbers have dropped, in the last three months, we have noticed a spike in attacks. For example, individuals and organizations have received spoofing emails seemingly from the Office of His Holiness the Dalai Lama. All the emails contain a Google Drive link and a key which is the password for the Zip file. However, if the file is downloaded and unzipped, it activates the MESSAGEMANIFOLD malware.
- Predictions for 2021:
- In the age of information technology, a click of a button can cause a huge impact. With the ongoing pandemic and multiple elections in the Tibetan community, it’s likely we will see more disinformation and misinformation being spread in the coming months. As we have already seen, such fakes news can spread far and wide in our community when people share information without verifying its accuracy.
- We might also see more fake accounts and online harassment in 2021. Since a user can submit any information when creating a social media account, fake accounts give people a sense of anonymity. While platforms such as Facebook and Twitter block accounts that are fake and that narrate hate speech, they can’t prevent and mitigate all the fake posts and content in circulation. Therefore, it’s up to every individual to break the chain by verifying information before sharing.
- Ever since the Indian government started banning Chinese apps, we have seen a rise in the number of cases of targeted attacks in our community. Before the bans, popular apps like WeChat and TikTok created risk for Tibetan users due to their easy exploitation by the Chinese government. However, since the ban, the number of Tibetans using Chinese apps has dropped exponentially. Given the reduction in easy access through the usage of these apps, we believe we might see even more targeted attacks via other means in the coming months.
- Digital Security Updates:
- Since the outbreak of COVID-19, we have seen a huge shift in everyone’s life, especially people who have to rely on technology and the Internet to either stay connected or for work. Many governments around the world have used this opportunity to collect more data, expanding their surveillance and monitoring of citizens in the name of helping to “mitigate COVID-19.”
- Firmware is software that is embedded in every device that is connected to the Internet. Unsecure firmware can be used to track you, steal your information, and control your system remotely. Given the many vulnerabilities that can be exploited, using devices such as Huawei and Oppo can bring a lot of cyberthreats.
- Cloud services continue to be popular and are widely used. However, new reports indicate that attackers can use vulnerabilities found in Cloud services like Google Drive in order to bypass security features to steal credentials of your Office 365, American Express.
- Apple notarization is a process of verifying an app for any security flaws and vulnerabilities before publishing it in the App Store. However, reports from a Mac security researcher show otherwise, detailing malware found in Apple devices that disguises itself as a Flash Installer.
- Tibet, located in the mountains of the Himalayas, has an ideal environment for servers to function properly. As a result, the Chinese government has established a data center that will fulfill the needs of Southeast Asian countries.
2. First Community-based TibCERT Response Hub
For more than a decade, the digital security team at Tibet Action Institute has focused on positively impacting the overall digital hygiene within the Tibetan community. With technology rapidly advancing, we have felt the need to use our resources to address tech support issues faced by different Tibetan organizations and institutions, as well as to create an updated awareness regarding the importance of digital security knowledge. The Chinese Communist Party (CCP) continues to be an undisputed adversary in our decades-long struggle, using various methods to bring an unprecedented number of cyber threats to our community in the diaspora. These cyber threats include constant phishing emails, socially engineered malware, and spyware attacks on various individuals and organizations that are intended to steal and misuse important data and strategies that can harm our Tibetan cause.
In consideration of such increasing cyber threats in our community, in 2016 Tibet Action Institute implemented a fellowship program. Through this program, individuals from Tibet Action began helping a few specific organizations with technical assistance, as well as assisting them in growing and maintaining critical digital security practices. With time, we saw the need to expand our services and include as many organizations and institutions as possible in order to reach a wide spectrum of our community. This is when the TibCERT project was launched.
Under the TibCERT project, we work with various organizations in the Tibetan community through a membership program, as well as collaborate with global technology researchers whenever possible. Our program provides technical support to its members, as well as bringing general awareness of the importance of digital security knowledge in the Tibetan community. The more collaboration we have with other organizations and individuals, the more we can learn about technical challenges faced by them due to the ever-increasing, targeted cyber threats from the Chinese regime. To help mitigate such threats, we provide digital security awareness to TibCERT members through basic digital security trainings, as well as the creation and implementation of digital security policies with the respective organizations. We also provide digital security incident response in order to mitigate phishing emails, socially engineered malware, and spyware attacks on the affected organizations. Much of our direct support and training work is enacted by four Digital Security Ambassadors (DSAs) deployed in major Tibetan settlements in India. TibCERT has also launched a help desk at support@tibcert.org where you can send digital security questions. Your email will generate a ticket and we try to respond to all queries within 48 hours.
In the TibCERT membership program, we currently have more than 40 participating organizations and institutions in India and have created a very successful support network for these entities. However, we have also seen the need to initiate a new program so as to reach a larger and more diverse network of Tibetans who are not members of TibCERT, allowing for wider support, threat management, and exchange of ideas and opinions on technical and digital security issues faced by these broader networks. To tackle this challenge, we have initiated a new program to establish volunteer-based, locally run Response Hubs in regions of India with large Tibetan populations. As of November 2020, we have successfully set up the first Response Hub in Dharamshala with 11 volunteers. In addition, in the coming months, we plan to establish two more hubs in Bylakuppe and Mundgod. We believe that this program will be very beneficial in helping to elevate the digital security knowledge and technical excellence of our community and, in particular at this time, focus on a common goal of creating awareness of misinformation and disinformation being spread through social media. In the future, we hope to extend our support capacity to other Tibetan communities outside of India, if possible.
The Response Hub program is based on four fundamentals:
- Learn:
Since Response Hub members come from different backgrounds, there is a great opportunity to learn from each other. While some members may be good at technical aspects or addressing social issues linked with cyber/online threats, others may bring strong skills in writing, influencing people, or graphic design. The Response Hub structure and environment provide ample opportunity for volunteers to skillshare and grow their abilities.
- Share:
The TibCERT Response Hubs prioritize a relaxed, connected, safe environment so that members can feel comfortable to share any issues they are facing and feel free to express their genuine opinions. By creating such a space, team members can feel free to share what’s on their minds without hesitation, nervousness, or fear of being wrong.
- Network:
One of the primary reasons for setting up the Response Hub program is to spread awareness, knowledge, and support on digital security issues for the maximum number of people in our community. Through the Response Hubs, the network of people we can reach is much larger and diversified than what can be done by TibCERT alone.
- Support:
The end goal of the Response Hub program is to provide technical support and digital security knowledge to all of the individuals and organizations reached through the TibCERT network. In order to do so, the practical solutions discussed and agreed upon by our Response Hub team members are systematically implemented to help provide the most comprehensive support possible.
Through the community-based Response Hub program, hub members gather together for discussions, problem-solving, and to determine how we can practically implement the solutions we discover. These discussion sessions or “meet-ups” occur once a month. Since the hub volunteer members come from different professional backgrounds, the diversity of views and opinions shared is a key factor in bringing creative and wide-reaching solutions to the broad range of technology and cyber issues faced by the Tibetan community today. We have also set up a secure online platform where our Response Hub members and anyone in the community who is interested can join and communicate with each other, share updates, and other relevant information regarding technology and digital security. With the unprecedented level of socially engineered malware attacks, phishing emails, censorship, and surveillance by the Chinese government, it is crucial that everyone in our community has at least a basic understanding of technology and the importance of digital security that will ultimately help the effectiveness and longevity of the Tibetan freedom movement.
3. Targeted Attacks in Our Community
3.1 Fake Accounts and Online Cyber Harassment
For many individuals, organizations, or corporations, social media accounts have become essential for staying connected, whether through Facebook, LinkedIn, Instagram, Twitter, or accounts on any other social media platform. However, social media can be a mixed blessing. While people’s shared posts, videos, pictures, etc. make the experience more interesting and help us connect with each other even when we are thousands of miles away, the ease in creating accounts has resulted in an exponentially increasing number of new social media accounts daily. With this has come a surge of fake accounts which, in most cases, are made with the intent of harming an individual or a group of people. The user can easily hide their true identity while having real-time and often serious effects on their victims. Unfortunately, some bad actors are always there to create discomfort and problems in the Tibetan community by creating fake profiles, spreading misinformation/disinformation harmful to the community in general, as well as targeting specific victims. This can include death threats, hate comments, blackmailing, repeatedly spamming into someone’s account, impersonating high profile individuals, and spreading malicious content, etc.
Since 2018, the Central Tibetan Administration (CTA) has organized an annual, in-person forum in Geneva. It has been an influential international platform where human rights advocates, activists, diplomats, academics, and politicians deliberate on and report human rights violations by the CCP. But given the ongoing pandemic, the 2020 Geneva Forum was held virtually on Facebook. The central theme this year was “The Global Impact of China’s Policy on Freedom of Religion.” The sessions were on how intolerance of religious practices in areas under China’s rule has led to the persecution of Tibetan Buddhists, Uyghur Muslims, Christians, and Falun Gong practitioners. During the live Facebook sessions, there were more than 50,000 hate comments sent during the five-day meeting from November 9th to 13th 2020. Throughout the discussions, people wrote highly offensive comments about the forum, its participants, and the human rights panelists that were presenting. Hate speech usually falls under the category of disinformation and misinformation because those spreading it are giving incorrect ideas and information about their targets to newcomers or new audiences, in this example those watching the live session. If we dive deeper into this particular forum in Geneva, for each session there were around 100 people watching live while more than 3,000 comments were left in the comments section each day (50,000 in total). This raises the question of whether or not these comments were genuine or from some group of people trying to disrupt the forum? Most of the profiles of the commentators seemed to be fake since when you check their profile, there are no friends or photos posted by the account holder besides the profile picture. And while the comments originated from different accounts, some of the comments were very similar to each other and, at times, exactly the same, indicating a coordinated campaign run by a group of people. “Studying the usage of Tibetan language in the comments, it could be assumed that the troll army also employs Tibetans from Tibet or Chinese netizens well versed in the Tibetan language,” said Tenzin Dalha of Tibetan Policy Institute on Phayul.
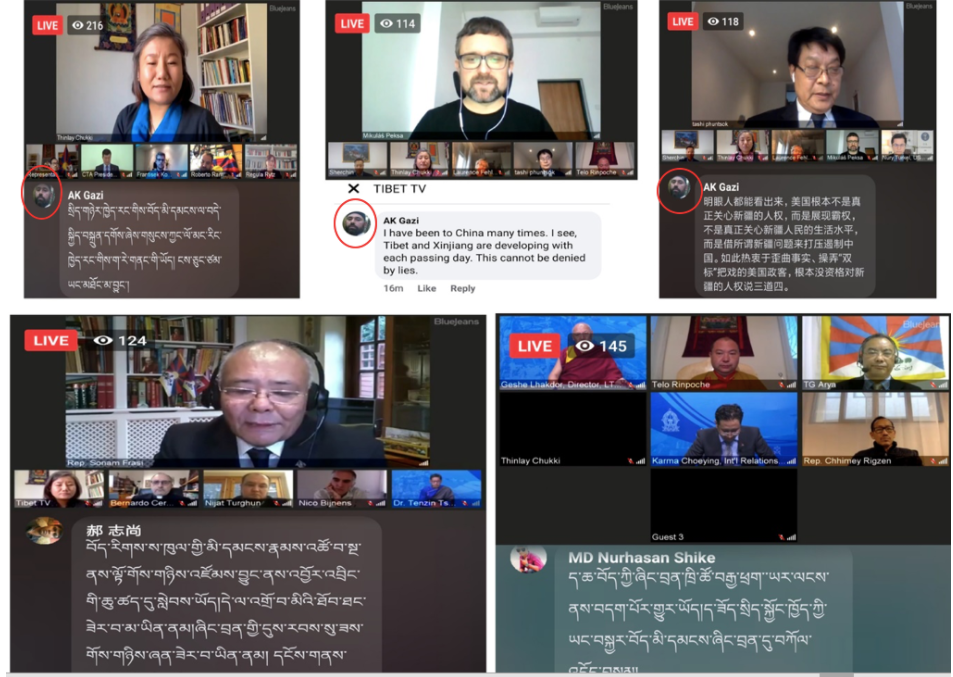 Figure 1: Comments from the same profile written in 3 different languages in 3 different contexts.
Figure 1: Comments from the same profile written in 3 different languages in 3 different contexts.
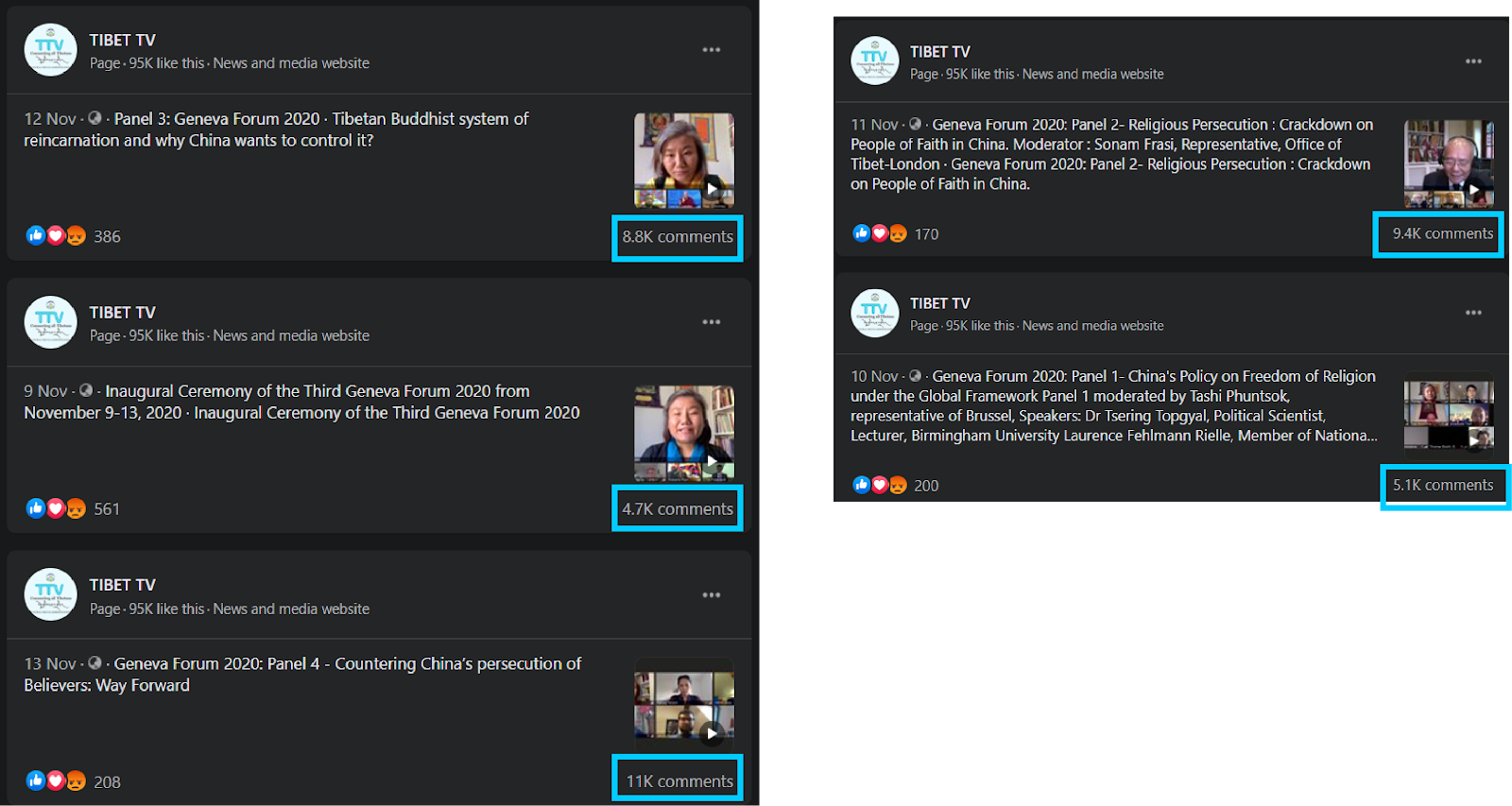 Figure 2: Two examples of the huge number of comments posted over the 5 days of online sessions.
Figure 2: Two examples of the huge number of comments posted over the 5 days of online sessions.
Many social media sites have their own understanding of hate speech. In the case of Facebook, they state, “Content that attacks people based on their actual or perceived race, ethnicity, national origin, religion, sex, gender, sexual orientation, disability or disease is not allowed.” They also add a significant note: “We do, however, allow clear attempts at humor or satire that might otherwise be considered a possible threat or attack. This includes content that many people may find to be in bad taste.” From October 2018 to March 2019, Facebook reported that it took down 3.39 billion accounts from the platform. Fake accounts are detected through a combination of artificial intelligence and human monitoring and most of them are blocked within a few minutes of their creation. Although social media platforms try to remove any suspicious accounts and hate comments that they find, they cannot fully remove them all, as we can clearly see the comments from those fake accounts during the 2020 Geneva Forum live session.
Since social media platforms lack the ability to fully control and prevent fake accounts from spreading hate/disinformation speech, there are some steps through which we can identify the authenticity of an account and how we can report it.
- How to identify if an account is fake or not:
- No profile photo, or only one photo but the account is two or three years old, or only has pictures of celebrities.
- Only common, well-known place names are used, for example, “Graduated from The Bronx High School of Science,” “Graduated from Harvard University,” and “Worked for CNN.”
- The account owner is in Pakistan but there are only foreign friends from the USA and literally no local friends.
- The content shift of an account is also an indication of red flags.
- Very little activity or interactions such as likes, comments, etc.
- Different names in the URL and the profile.
A detailed explanation of the above steps are on our website at: https://learn.tibcert.org/knowledge-base/how-do-we-know-if-the-facebook-account-is-fake/
- When you come across a fake account, we highly recommend you report it to the respective platform by following the set of guidelines provided by the company. In addition, it is a good idea to take screenshots or print out the profile of the account as evidence in case requested by authorities. You can also visit our website at https://learn.tibcert.org/knowledge-base/how-to-report-content-or-fake-profile-in-facebook/ on how to report a fake account on Facebook or you can reach us at support@tibcert.org for assistance.
3.2 Ransomware Attacks in Our Community
In the third quarter of this year, we saw a huge surge in ransomware attacks. Globally, a total of 199.7 million such attacks were reported in the third quarter of 2020 alone. In short, a ransomware attack is a form of malware that encrypts a victim’s files/drive so the user cannot access their own information. The attacker then demands a ransom from the victim to restore access to the data upon payment. Everyone is at risk of ransomware. If you have any type of public-facing platform such as a social media account, website, or even just your personal computer or office desktop, you can be a potential target of ransomware.
While most people have no idea how a ransomware attack occurs, it is important to know that the most common deliveries are malicious links or attachments that come via email, masquerading as a file that looks like something trustworthy. Once you’ve downloaded the attachments and opened them, they can take over your device, allowing attackers the administrative access to make changes in your device, in this case, encrypting folders or drives. The best way to mitigate ransomware attacks is by keeping backups of your data, since there’s no guarantee whether you’ll actually be able to recover your file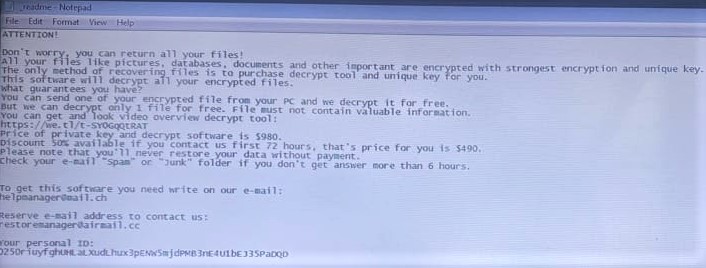 s even after paying a ransom. In fact, we strongly recommend you keep a backup of your backup as well, in case your backup also crashes or is lost.
s even after paying a ransom. In fact, we strongly recommend you keep a backup of your backup as well, in case your backup also crashes or is lost.
Not long ago, a few ransomware cases occurred in the Tibetan community. In one instance, a whole server was encrypted by attackers who then asked for a ransom to decrypt the server. In another case, the attacker encrypted only some parts of files in the computer which was still very disruptive. The type of encryption used in this latter instance was “.ogdo” which falls into the category of Ogdo ransomware. Ogdo is a malicious program which is part of the Djvu ransomware group and is specifically designed to encrypt data for ransom. As shown in the figure below, during the encryption process, all of the compromised files were appended with the “.ogdo” extension. For example, the original file titled “2010-TCV teaching Buddhism 4\01\VIDEO_TS.BUP” changed to “2010-TCV teaching Buddhism 4\01\VIDEO_TS.BUP.ogdo” following encryption. After this process is completed, ransom-demanding messages “readme.txt” are created and dropped into affected folders. The ransom note (“_readme.txt”) states that all of the victim’s data has been encrypted with the strongest encryption and a unique key. The message reassures users that they can recover their files by purchasing the decryption keys and software from the cybercriminals behind Ogdo ransomware.
 Figure 3: Screenshot of files encrypted with the extra extension “.ogdo” after the actual file name.
Figure 3: Screenshot of files encrypted with the extra extension “.ogdo” after the actual file name.
 Figure 4: The readme text asking for ransom payments to recover the encrypted files.
Figure 4: The readme text asking for ransom payments to recover the encrypted files.
In order to avoid ransomware attacks, there are some preventive measures we can take:
- Think Before You Click: Always think twice before clicking on suspicious or random links in unsolicited emails.
- Detach From Attachments: Do not open or send email attachments to help avoid malware attacks.
- Keep Backups of Data: Create a separate data backup in an external hard drive that is not connected to your computer. This way you won’t have to pay a ransom for an attack.
- Never Disclose Your Personal Information to Any Unfamiliar Sites: Do not provide personal information when answering an email, unsolicited phone call, text message, or instant message. Phishers will try to trick employees into installing malware or gain intelligence for attacks by claiming to be from a trusted service provider.
- Don’t Wait, Update: Make sure that all systems and software on your devices are up-to-date with the latest patches. Exploit kits hosted on compromised websites are commonly used to spread malware. Regular patching of vulnerable software is necessary to help prevent infiltration.
- Do Not Pay the Ransom: Payment only encourages and funds these attackers. Even if the ransom is paid, there is no guarantee that you will be able to regain access to your files.
To learn more about the importance of data backup and best practices with regard to backups, please refer to https://learn.tibcert.org/knowledge-base/importance-of-data-backup-and-recovery/.
3.3 Rise in Malicious Emails Received by our Community/Targeted Threats through Email
Our community has been receiving socially engineered emails from the Chinese government for more than a decade. However, we have noticed that the number of email attacks has decreased over the last few years. But ever since the Indian government began banning Chinese apps, the number of email attacks has spiked again. For example, we have seen different malicious emails received by TibCERT members which are all connected to each other in some way. Given the drastic reduction in the number of users for Chinese apps, we can hypothesize that the increase in email attacks could be correlated with the reduction in vulnerability for attacks via Chinese apps.
In the month of October 2019, we discovered some malicious email attacks targeting our community. In one instance, the sender sent an email pretending to be from the Office of His Holiness the Dalai Lama (OHHDL). This was an example of email spoofing in which the attacker fabricated the header of the email in hopes of tricking the recipient into thinking the message is from the intended source. In this case, the body of the email consisted of a Google Drive link that would download an executable file when clicked, installing malware on the recipient’s device. 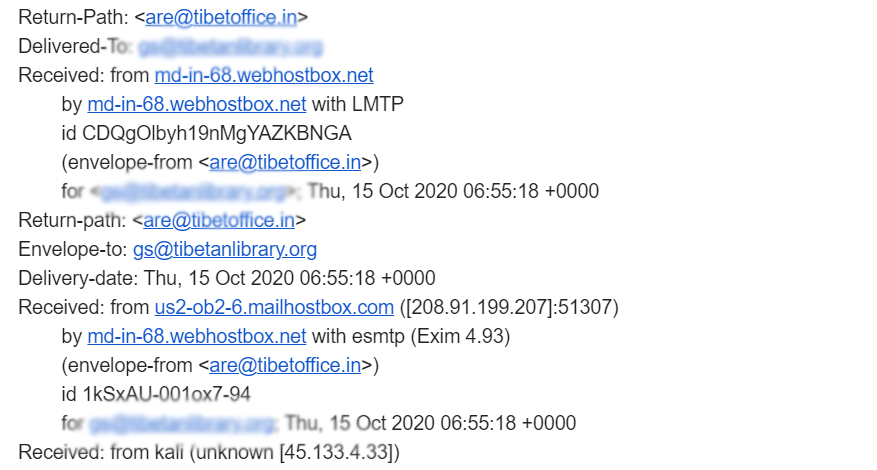 Figure 5: Email header where the sender is md-in-68.webhostbox.net
Figure 5: Email header where the sender is md-in-68.webhostbox.net
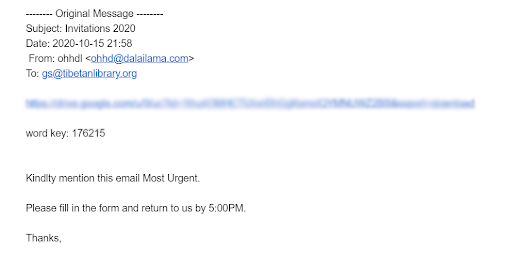 Figure 6: Fake email received from attacker consisting of a Google Drive link
Figure 6: Fake email received from attacker consisting of a Google Drive link
A similar email with the same email id was sent to another individual including the same Google Drive link. It looks like the attackers are well aware that our community doesn’t easily open random attachments and unknown links given a growing knowledge of the risks. Instead, they sent the malware through Google Drive since many people are aware that Google can detect malware and remove it as soon as it detects it, making it a less risky bet. However, since this corrupted Google Drive file was zipped and password-protected, it cannot be scanned for malware. Taking advantage of this vulnerability, the attacker sent a zip file in Google Drive containing MESSAGEMANIFOLD malware. This was part of a “spear-phishing” campaign targeting the Tibetan community that was previously used to attack the Taiwanese legislature. The executable file dalailama-Invitation.exe is in the Google Drive link and, when clicked, a window error pops-up and automatically downloads an executable file to “C:\users\public” of the infected device.
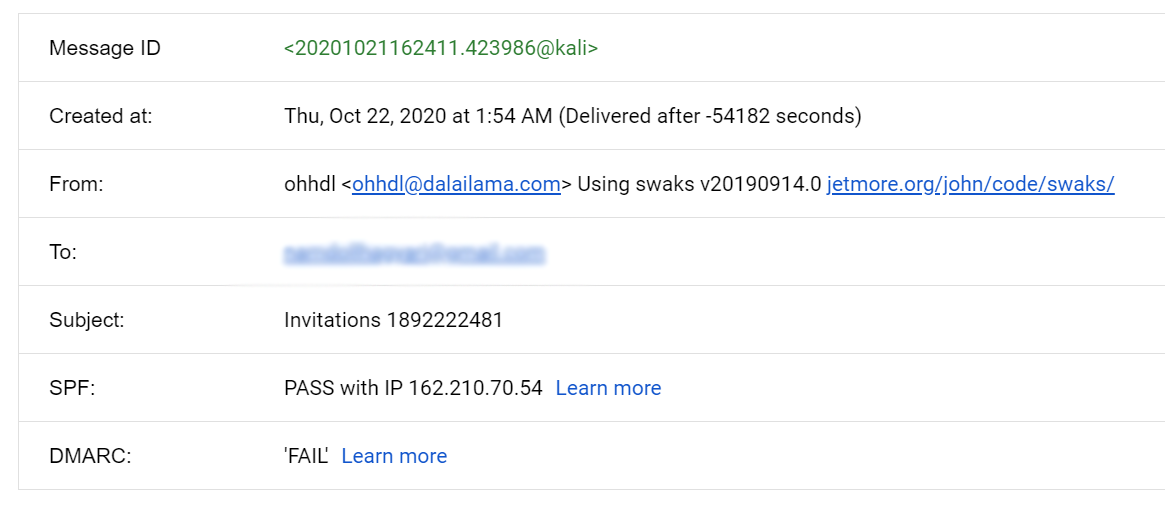 Figure 7: Fake email id of OHHDL using the website jetmore.org
Figure 7: Fake email id of OHHDL using the website jetmore.org
On the 19th of October, 2020, there was another email spoofing attack pretending to be from the Office of His Holiness the Dalai Lama. This email contained a link to a .pdf attachment. The sender’s email appeared as ohhdl@dalailama.online which is not a legitimate email address. When analyzing the email, we found that the attacker had given fake details while registering the spoofing email account.
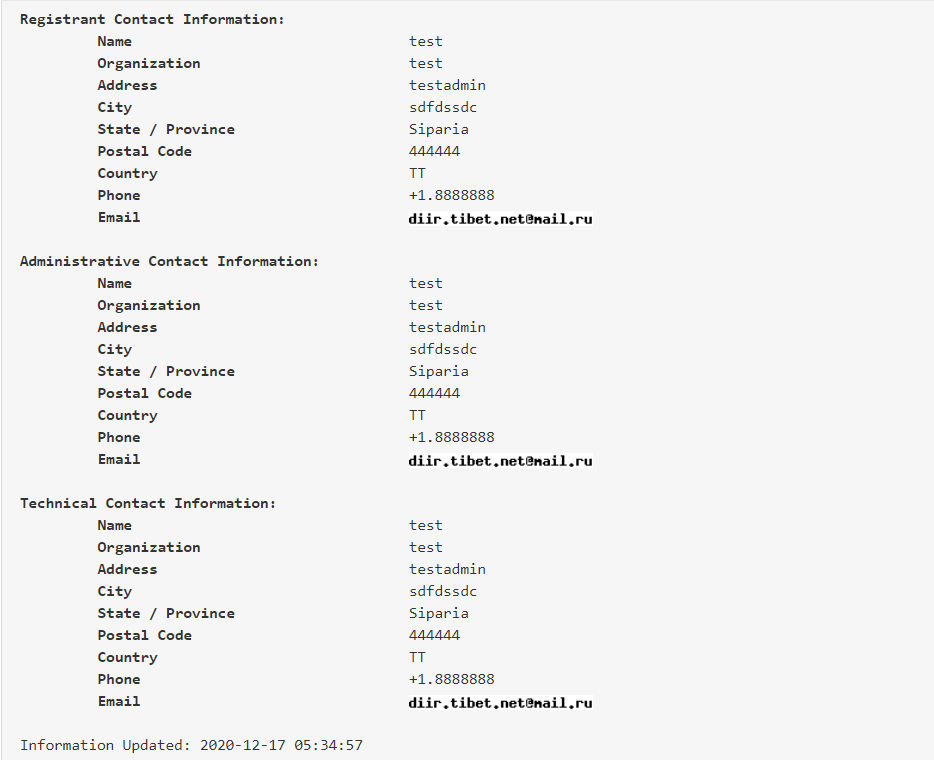 Figure 8: Background details of the email account is baseless and fake
Figure 8: Background details of the email account is baseless and fake
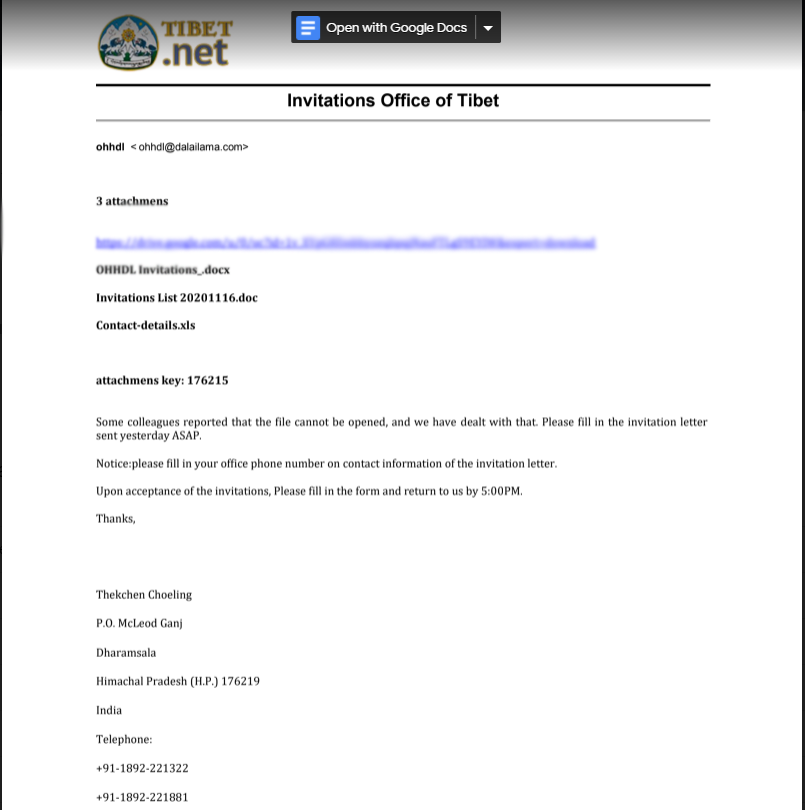 Figure 9: Email consisting of this .pdf with a Google Drive link inside it
Figure 9: Email consisting of this .pdf with a Google Drive link inside it
Through a search on www.whois.com, we have determined that the registrant’s contact information is all fake and the dalailama.online was created just a few days before the email attack, as shown in the figure below.
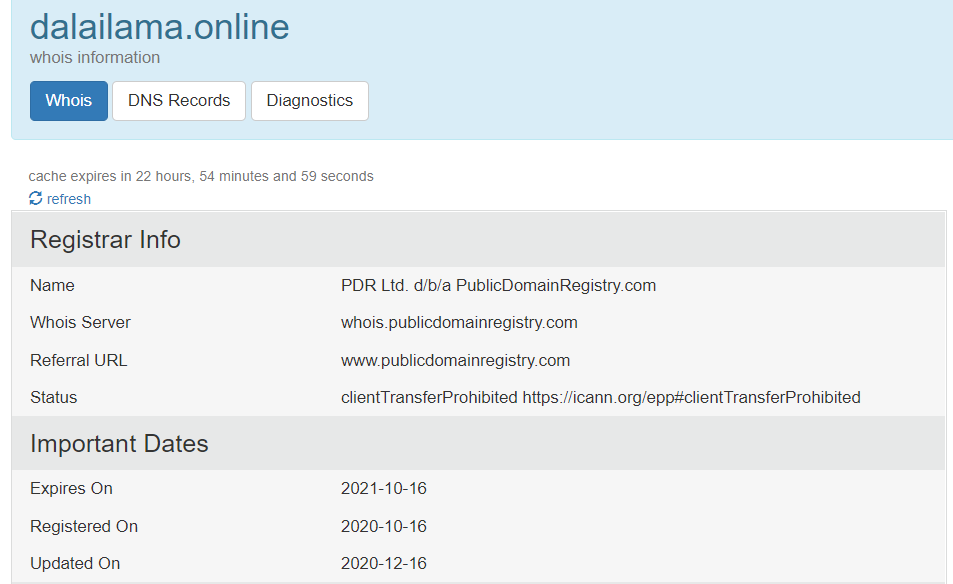 Figure 10: dalailama.online was created a few days before the actual email was sent
Figure 10: dalailama.online was created a few days before the actual email was sent
TibCERT solutions:
With ongoing threats, it remains extremely important to continue utilizing best practices for avoiding attacks. Once again, you should always:
- “Think Before You Click – Whenever you receive an email from an unfamiliar sender, it is crucial to verify the email address and make sure it is someone you can trust. Also, always beware of links. Before clicking a link, you can verify it by copying the link into https://virustotal.com and scanning it for potential malware.
- Detach from Attachments – An attachment such as a Word Document, PDF file, or any type of file can be weaponized with malicious software that can be used to infect your computer when opened. The best alternate approach for sharing information is to use Google Drive instead of attachments. However, to avoid vulnerabilities, only use the preview option to view a document rather than downloading it and avoid files like .exe for Windows, .dmg for Mac, and zipped files in general since Google can not scan them for any malicious content. You can also refer to our knowledgebase website https://learn.tibcert.org/ to help better understand other best practices.
- Don’t Wait, Update – Developers purposely make software updates to patch the security holes. If you don’t update on time there will be a security hole that attackers can utilize to enter and compromise your device. Therefore, make sure you update your software as soon as it is available.
Be a 30-Second Email Detective – Since email threats are continuously increasing, understanding how to detect suspicious emails will surely reduce the risks presented by email threats.
- Check whether you recognize the email sender.
- Check if it’s a recognized sender but with a different domain.
- Check for misspelled words in the email name.
- Always beware of attachments or suspicious links, even from a trusted sender.
4. Predictions for the Coming Year
4.1 Disinformation and Misinformation
Today, the dominance of the internet in our personal and professional lives cannot be denied. In this age of information, people around the world can exchange facts, views, opinions, and ideologies through the click of a button. However, the difference between exchanging information and opinions in real life and doing so on the internet can be a totally different scenario. When people exchange their opinions and ideologies sitting face to face, they are often more careful with their words. On the other hand, the internet has become a platform where people can post almost anything online, regardless of whether it hurts other people or if the information itself is genuine or not. The dark side of the internet is this false sense of anonymity many people feel while they are online and, as a result, don’t care or think about the potential negative effects of content they post online. Some do it deliberately while others do it out of sheer naivete.
As detailed in our 4th issue of the bulletin, the spread of misinformation (sharing false information without verifying its content) and disinformation (deliberately spreading fake content with the intent to harm) are serious issues facing the Tibetan community. As the 2021 Tibetan Sikyong and Parliamentary elections are nearing, we could face an unprecedented challenge to our democracy and fair electoral processes through the spread of harmful misinformation and disinformation. We must not let our varying ideologies (e.g., from different schools of Tibetan Buddhism or regional backgrounds) or personal opinions regarding candidates lead to unnecessary divisions via character assassinations or misleading representations. It is important always, and particularly at this moment with regard to the election, to remain vigilant against false information. For example, in the month of September 2020, a fake letter went viral in the name of His Holiness The Dalai Lama. The letter urged Tibetans to elect a leader that could continue to work with dedication like the current CTA President Lobsang Sangay and not a candidate who is “controversial and questionable.” While the Office of the Dalai Lama issued a statement that the letter was fake, it is a clear example of a misleading message to defame His Holiness the Dalai Lama, influence voters, as well as cause disruption in the unity of Tibetans in the diaspora.
 Figure 11: A fake letter about the upcoming election pretending to be from OHHDL.
Figure 11: A fake letter about the upcoming election pretending to be from OHHDL.
During an August 5, 2020 press conference, the Tibetan Election Commission issued guidelines urging everyone to take individual responsibility and be careful not to spread misinformation and disinformation through social media platforms that could negatively affect a free, fair, and respectful electoral process.
Beyond the election, the ongoing pandemic continues to provide a breeding ground for the spread of false information. At the beginning of the 2020 lockdown in India, a lot of COVID-19 related mis/disinformation went viral, manipulating people’s faith in science and religion. With the ongoing pandemic, we believe news related to COVID-19 may keep spreading without proper verification. In particular, as many countries distribute COVID-19 vaccines, it’s critical to be careful about possible fake news regarding how effective or ineffective the new COVID-19 vaccines are. Furthermore, in the coming days, there is a huge possibility that we may encounter misinformation and disinformation regarding the new strain of COVID-19 emerging from the southeastern region of the U.K, dubbed as VUI-202012/01. It is very important that until proper research is available on this new strain of the virus, we shouldn’t simply take as the truth any information shared with us through the media or our community circles.
In addition, CCP state-sponsored disinformation campaigns continue to emerge through a wide range of fake social media accounts, predominantly Facebook, WeChat, and Twitter. The most recent example is the online Geneva Forum with its central theme on the “Global Impact of China’s Policy on Freedom of Religion.” It was hosted live on Facebook where fake accounts in multiple languages posted more than 50,000 comments over three days, propagating false CCP narratives. These fake accounts are most likely run by the 50 Cent Army, a CCP-sponsored entity. According to Phayul, “The government-employed troll army proficient in multiple languages, reportedly numbering from five hundred thousand to two million, works to post comments on the Internet, praising the image and integrity of the CCP and attack its critics with the intention of fabricating facts as well as removing content deemed as unfavorable.” The attacks of the 50 Cent Army have grown exponentially due to the COVID-19 pandemic and the rise of individuals and organizations engaging in online activities such as virtual official meetings to conferences.
TibCERT’s Solution:
- Given the escalating level of mis/disinformation, we should always cross-check for official and verified sources of information for any news and posts seen on social media and other media platforms. Information shouldn’t be shared without prior fact-checking. This is why the “Think Before You Share” concept is essential to help mitigate the potential harm done by sharing and believing in false and unverified information.
- Please contact our help desk at support@tibcert.org to report any fake or doubtful information you see circulating within our community. We will generate a ticket to your email query and do our best to respond within 48 hours.
- Reporting Fake Accounts and Disabling Spam Comments from Fake Social Media Accounts
For any fake accounts found on Facebook, one can go to the profile and report the account.
-
-
To manage spam and hate comments on Facebook live meetings and conferences, we can use the comment moderation feature to limit or disable comments made by newly made fake accounts or comments made without following the live sessions for a specific duration of time.
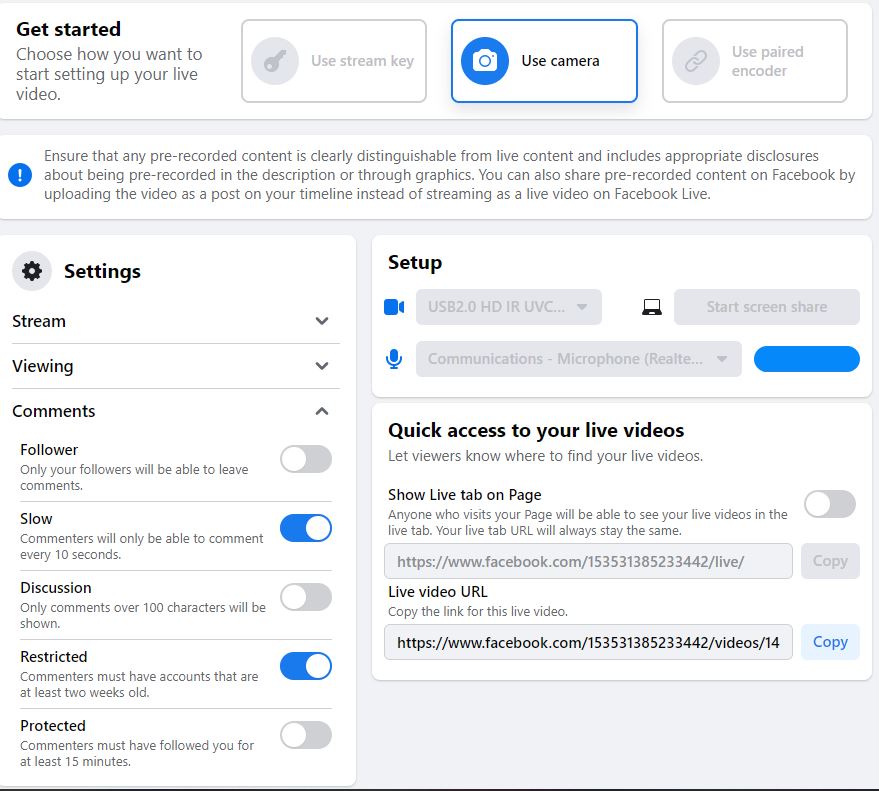
-
4.2 Online Fake Accounts, Spam, and Hate Comments People have always been looking to connect and network with each other. Today, people are shifting from postal delivery letters to emails, landline phone calls to video calls, and from newspapers to news apps. In this age of digitization, people have found ways to be socially interactive on the internet through popular social networking platforms such as Facebook, Instagram, Snapchat, Twitter, etc. In 2020, there were 3.8 billion people actively using social media in this world, an increase of 9.2% from 2019. Back in 2015, there were only 2.07 billion users. Along with the rising number of social media users, there are also more fake accounts. Facebook estimates that 5% of accounts on the platform are fake accounts, or more than 90 million, a figure that hasn’t budged for more than a year.
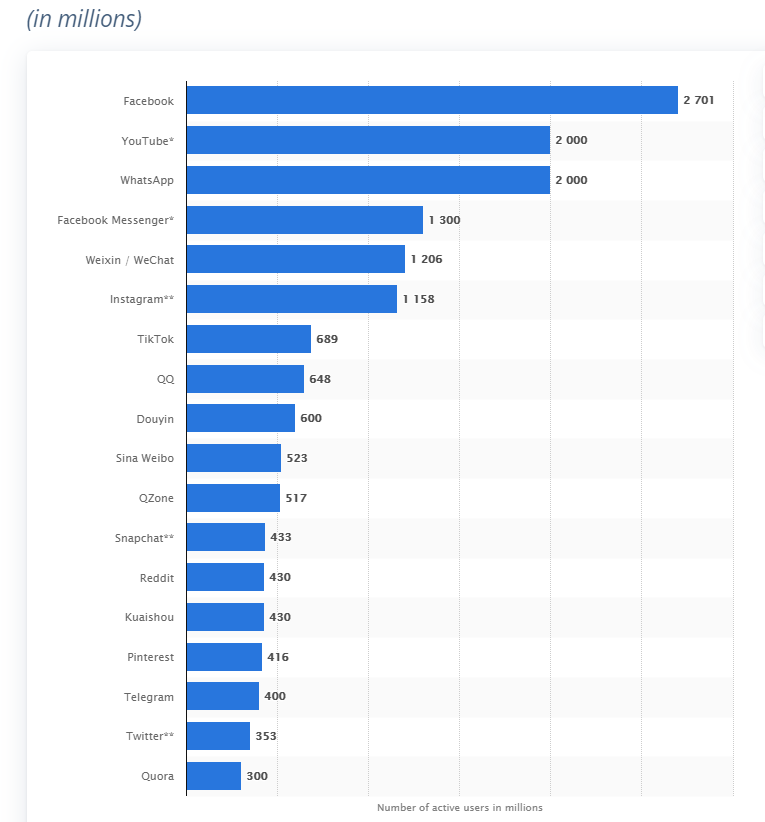 Figure 12: social network platforms as of October 2020, ranked by number of active users
Figure 12: social network platforms as of October 2020, ranked by number of active users
The issue of fake accounts can seem never-ending, with another billion fake accounts removed every few months. It is clear that fake accounts are not going to stop any time soon, with ongoing spam messages and hate comments continuing to impact their victims. But there are a few mitigation strategies we can implement to lessen the impact of spam and online hate comments.
Before going live on Facebook, for example, there are some settings we can manage to give less flexibility to fake accounts and hate comments. Go to Settings and under Comment Settings, you can:
- Enable only your Followers to be able to leave comments.
- Slow commenters down so they can only comment every 10 seconds.
- Activate Discussions so only comments over 100 characters will be shown.
- Turn on Restricted comments so commenters must have accounts that are at least two weeks old.
- Use the Protected setting so that commenters must have followed you for at least 15 minutes.
5. Digital Security Updates
5.1 Increase in Surveillance and Censorship Worldwide Due to COVID-19 Excuse
2020 was a year in which the pandemic affected everyone, forcing people to work from home and stay indoors, so eventually the use of technology and the internet spiked. This opportunity was taken by governments around the world to introduce new and effective digital surveillance and data collection tools to combat COVID-19. However, new reports are surfacing stating that those technologies are actually being used as an abuse of power.
According to Freedom House, a human rights watchdog group, there has been a decline in global Internet freedom over the last 10 years. But with the outbreak of COVID-19, we have witnessed a major rising abuse of new digital surveillance technologies. Political leaders and authorities are using the ongoing pandemic as an excuse to limit access to information, at times blocking independent news sources and arresting whistleblowers speaking out against the spread of rumors and misinformation. In some cases, various government agencies have used misinformation to hide the real issues, using COVID-19 as an excuse to extend surveillance and deploy new and intrusive technologies. As such, the public healthcare crisis has opened up an opportunity for authorities to digitize, collect, and analyze people’s most intimate data without adequate protection against abuses. It has also led to an increase in artificial intelligence (AI), biometric surveillance, and big-data tools to make decisions that affect the economic, social, and political rights of individuals.
In particular, with the onset of COVID-19, China has increased surveillance and censorship technology to avoid the spread of the virus. However, the CCP has simultaneously used this tech to help stop the free flow of information and squash criticism of the government via automated censorship, high-tech surveillance, and contact tracing.
5.2 Firmware Vulnerabilities
Today’s computers, smartphones, or Internet of Things (IoTs) use software, some of which come preloaded on the device while others we download and install. An important concept that everyone should know is that technology keeps advancing and with that, every software is bound to have some vulnerabilities and bugs over time. One such software that comes along with your device is called Firmware. Firmware is a software program or set of instructions programmed on a hardware device. It provides the necessary instructions for how the device communicates with the other computer hardware. Firmware is typically stored in the flash ROM of a hardware device. While ROM is a “read-only memory,” flash ROM can be erased and rewritten because it is actually a type of flash memory.
Why Does Firmware Security Matter?
Firmware security by default isn’t as secure as it should be, especially in the Basic Input/Output System (BIOS) of most computers. A single device contains tons of firmware such as a webcam or sound card or display, etc. Since malware can be embedded in firmware or it can be hacked, firmware can pose a huge risk to your computer and phone since firmware producers usually don’t design their firmware with security in mind. Firmware malware will exploit this lack of security by attaching its code to the firmware’s code. Since the firmware isn’t secured by a cryptographic signature, it won’t detect the infiltration and the malware will be hidden within the firmware code.
What Are the Biggest Firmware Security Threats?
A lack of firmware security opens you up to the same risks you’re exposed to if you don’t know how to prevent phishing or business email compromise, or any other cyber threats out there. Through firmware malware, attackers can::
- Initiate remote control of your system
- Secretly spy on you
- Exfiltrate your activity
Huawei Firmware
In 2019, Huawei unveiled its own OS. It was primarily designed to work with its IoT devices. Harmony version 2.0 beta was announced on Dec 16, 2020, with support for smartphones, head units, watches, and smart TVs. Harmony can run Android apps and functions just like Android phones but it is not another version of Android. Unlike Android’s monolithic kernels, Harmony is based on Microkernel. A Microkernel is more modular.
Like any other tech company, Huawei follows the same restrictive internet policy initiated by the Chinese government, yet it was also reported that Huawei received huge state support that helped it grow into the leading 5G network gear supplier it is today. According to the Washington Journal, Chinese government assistance helped Huawei grow the world’s largest telecommunications equipment supplier, allowing it to offer generous financing terms and undercut rivals’ prices by some 30 percent.
Risk of Using Harmony OS
Harmony OS maker Huawei has been in the news for all kinds of rumors related to security and privacy issues. The United States has recently banned Huawei 5G infrastructure in the U.S. along with all ties with U.S. companies due to its close relationship with the Chinese government. Australia and some European governments have also banned companies from any sort of dealing with Huawei for fear that the Chinese government is using the company’s products to spy on users outside of China.
Oppo Firmware
Oppo is another Chinese electronics and mobile communications company and Oppo Stock ROM is the Official System (OS) of Oppo smartphones. The Stock ROM can be used to reinstall the operating system (OS), if in case you are facing any software related issues, boot loop issue, or IMEI issue. The Oppo Stock ROM can also be used to upgrade or downgrade the operating system (OS) on Oppo devices. Given the company’s ties to the Chinese government, there is an inherent risk of surveillance for users of Oppo firmware
Risk of Using Stock ROM Downloaded From the Internet
- The risk of using Stock ROM that is downloaded from the internet is that third-party Stock ROM can masquerade as genuine Stock ROM. If you unintentionally install one of those ROMs then your data might be at serious risk from attackers.
- Stock ROM provided by tech companies is usually safe. However, since all Chinese tech companies are surveilled by the Chinese government, even if you use Stock ROM provided by the company, your data might still be at serious risk. Research has shown that Chinese companies install a backdoor in smartphone firmware which exposes a lot of user information to various governmental bodies. Information that is collected and transmitted includes:
- Full-body text messages
- Contact lists
- Call history with full telephone numbers
- Unique device identifiers including the International Mobile Subscriber Identity (IMSI) and the International Mobile Equipment Identity (IMEI) from a user’s phone.
For example, in 2019, a vulnerability was found in Oppo firmware in the form of a preinstalled platform app. This app cannot be disabled by the user and the attack can be performed by a zero-permission app. The malware acts as the admin of the device which can allow a third-party app to video record the user’s screen, factory reset the device, obtain the user’s notifications, read the logs, inject events in the Graphical User Interface (GUI), obtain the user’s text messages, and more. This vulnerability can also be used to secretly record audio of the user.
How Do You Implement Firmware Security?
Firmware security is largely in the hands of hardware makers since it is the industry’s role to design their products to withstand malware infections and to release updates to fix security vulnerabilities when needed. However, there are several actions we can take to help keep our firmware secure.
- Update firmware as soon as the vendor releases it
You should update your firmware to the latest version as quickly as possible to close any security holes and ensure the proper functioning of your hardware.
- Don’t use untrusted USBs
USBs are highly insecure and dangerous to use. A smart hacker can store malware into the firmware of the USB device itself. We suggest only using USBs that have been exclusively handled by you and you only.
- Buy hardware with built-in protection against malicious firmware
The best step you can take is to buy hardware with built-in firmware security. BIOS vendors, among other hardware companies, are continually updating their security in light of past firmware vulnerabilities.
5.3 Using Google Services (Docs, Sheets, Forms, etc.) to Weaponize and Bypass Security Features.
Due to the COVID-19 pandemic, organizations have adopted a work from home model with many using Google or Microsoft services. Recently, there have been new ways of weaponizing those infrastructures, with attackers increasingly abusing vulnerabilities found in Cloud services like Google Cloud services. In order to increase legitimacy and fool security filters, attackers have begun using Google services such as Google Forms, Google Docs, and Firebase.
Attack Using Google Form to Acquire American Express Credentials
In October 2020, an attack was orchestrated using Google Form where the attacker used the American Express logo as branding to capture the user’s American Express credentials card information, and other sensitive data. Research shows that a phishing link hosted on Google Form can bypass any security filters blocking known bad links or domains. Since the Google domain is reliable and Google Forms are widely used by many organizations, it will be unlikely to get detected by email security filter thus payload will be successfully deployed
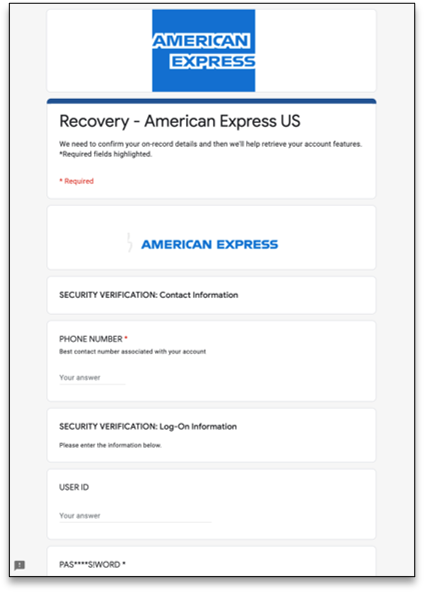 Figure 15: Phishing page for the AmEx attack was hosted on a Google Form
Figure 15: Phishing page for the AmEx attack was hosted on a Google Form
Microsoft Teams Credential Phishing
In another case, the attacker sent an email impersonating Microsoft’s IT team, asking victims to review the secure message their colleague has shared over Microsoft Teams. By clicking the link, the victim is redirected to a page that looks just like the Microsoft Team, which will then redirect the user to the credential phishing site resembling the Office 365 login portal.
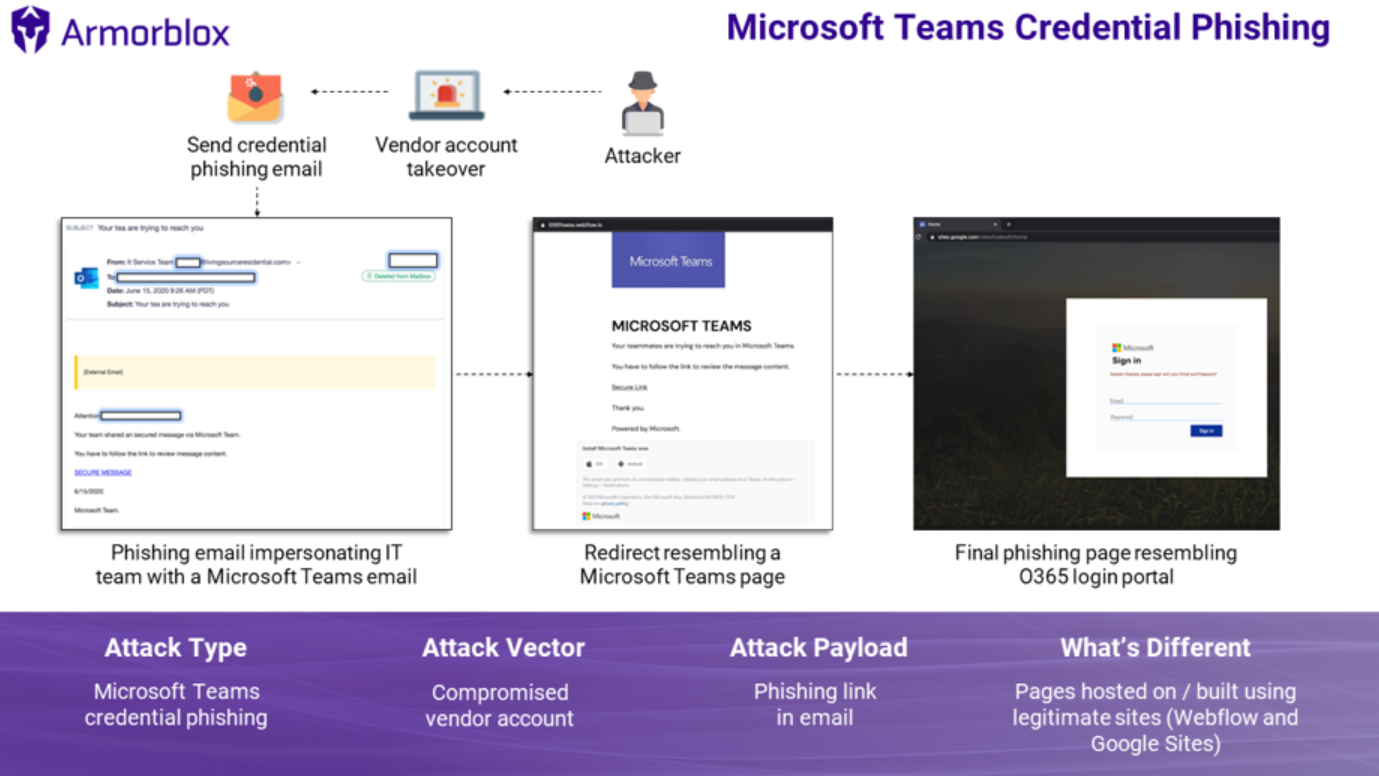 Figure 16: Summary of the Microsoft Teams credential phishing attack
Figure 16: Summary of the Microsoft Teams credential phishing attack
Why Those Attacks Got Through Undetected
Both the Google and Microsoft attacks successfully got past the email authentication checks since they were sent via a legitimate domain and both the phishing pages were hosted on legitimate sites that enabled them to slip past firewalls and filters that block bad known domains. It is also a socially engineered email to steal credentials that will trick you into entering your credentials on fake websites. Therefore, it is easy to slip past you if you don’t do any basic email verification. Even then, some emails are hard to catch without carefully examining them since the information can seem real and personal to you.
5.4 Apple-Notarized Malware: What Is It and How Does It Affect Mac Users?
What is Apple-Notarized?
In 2019, Apple started a notarization process through which software developers must submit their apps for security checks before being allowed to run on Apple devices. The process involves an automatic check for certificate issues and any suspicious code on the apps. If the app completes the verification process and clears this exam then the app gets a notification ticket or security approval ticket from Apple for the app to be able to stay on the App Store and run on Apple devices.
What is Apple-Notarized Malware?
Apple-Notarized Malware is malware that has been notarized to run on Apple devices. Apple uses a notarization mechanism to increase Apple device’s security by detecting and blocking malicious apps from being downloaded on an Apple device. Well-known Mac security researchers Peter Dantini and Patrick Wardle found a malware campaign disguised as an Adobe Flash installer, which is common and has been around for years. Usually, Macs block this type of malware immediately when opened. However, the researchers found one malicious Flash Installer that has code notarized by Apple and can run on Apple Devices. This means that Apple had scanned the code and Apple was not able to find any malware, so it had notarized it accidentally.
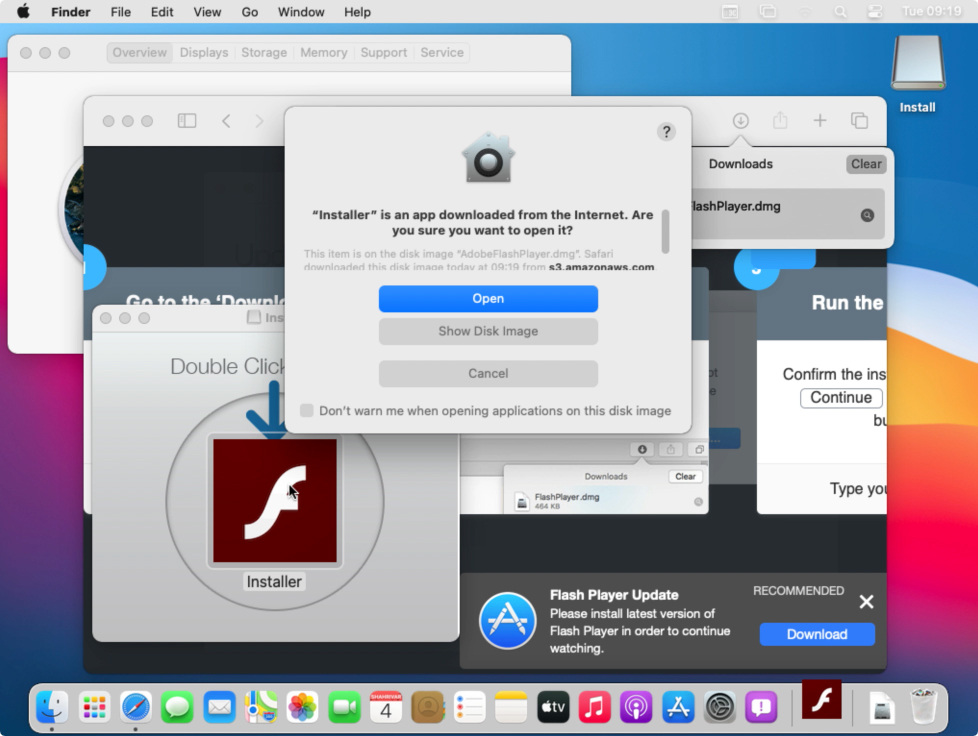 Figure 17 : The malicious Flash installer notarized by Apple
Figure 17 : The malicious Flash installer notarized by Apple
How It Affects Apple Device Users?
Since the malicious Adobe Flash installer potentially exposes Apple device users to malware, this essentially means the App Store is not 100% malware-free or foolproof. “Apple revoked the notarized payloads when Wardle reached out, preventing the malware from running on Macs in the future.” “But Wardle said that the attackers were back soon after with a new, notarized payload, able to circumvent Mac’s security all over again. Apple confirmed to TechCrunch it has also blocked that payload. The cat and mouse game continues.” Given this ongoing potential threat, it is very important for users to help protect themselves against malware by following and implementing best security practices (see above), at the same time keeping well-informed on cybersecurity developments.
5.4 Construction of The Highest Data Center in TAR
China is using Lhasa, the capital city of Tibet, to build the highest altitude Cloud computing data center, standing at around 3,656 meters above sea level. This center will fulfill the data storage requirement of China and many South Asian countries as reported by state-run Xinhua news agency.
The facility stretches over 645,000 square meters with its temperate climate and low average temperature that are ideal for keeping servers cool, thereby reducing costs for running data centers compared to other Asian countries. This pushes forward Tibet into becoming a big data industrial base. The total planned investment is 11.8 billion yuan (over USD 1.80 billion) for the project. The project will provide services in areas such as video rendering, autonomous driving, distance-learning, data backup, and others, to major Chinese provinces and cities, as well as Nepal, Bangladesh, Pakistan, and part of Southeast Asia.
Chinese commerce giant Alibaba signed a massive agreement with Lhasa-based operator Ningsuan Technology Group (NTG) to bring Alibaba’s cloud computing business into the Tibetan region across different sectors like electricity supply, finance, national security, government affairs, public security, and cyberspace. The first phase is expected to start in 2021. After the completion of the first phase, the project is expected to generate an annual revenue of 1.5 billion yuan (about USD 223.5 million) according to NTG as reported on The IndianEXPRESS news website.