Cellular network attack on a high-level Tibetan functionary.
Mar 14, 2025
🚦 TLP: WHITE
(Indicates that this information is the least restrictive classification, and can be shared freely with the public without limitations.)
Background
- On March 14, 2025, we were contacted with a request from a high-level Tibetan functionary, who reported receiving multiple abnormal roaming messages from his cellular provider stating “Welcome to China”.
Summary
-
The combination of signal loss, call interference, and multiple “Welcome to China” messages points to a sophisticated attack rather than a benign error or coincidence.
-
During our incident response, we analyzed the victim’s phone logs and traffic data, finding no suspicious activity or anomalies to suggest the phone was compromised.
-
Initially, our hypothesis was that the victim phone was targeted with a SIM cloning attack, but after consulting with an expert, we realized it was not a SIM cloning attack but a Cellular Network Attack.
-
The attacker likely obtained the victim’s phone number and used advanced cellular network methods(such as IMSI catcher1 or using IPX operator2 and HLR query3) to identify the target’s IMSI4 number.
-
The attacker could have gained access to the victim’s phone by manipulating device network registration using SS75 and DIAMETER6, or traffic steering techniques to track the victim’s device’s location, monitor its movement, and identify its contacts.
Investigation Process,
As we conducted our investigation, the initial concern that emerged was the potential compromise of his phone. We asked the victim a few questions, including his thoughts on why he might have received such messages, along with additional inquiries such as whether he experienced loss of cellular signal, background noise during calls, and the specific “Welcome to China” SMS messages from his cellular provider.
We came to know that he has experienced abnormal activities with his mobile phone which are as follows:
- Loss of cellular signal
- Background noise during calls
- Multiple “Welcome to China” SMS message from the cellular provider
Loss of cellular signal: The device experienced signal drops, which could indicate network congestion or poor network coverage. The signal loss alone is not conclusive but paired with other indicators, suggests a coordinated issue beyond typical network fluctuation.
Background noise during call: Unexplained noise during calls could come from poor signal quality, device malfunction, man-in the middle attack or Cellular Network Attack.
“Welcome to China” SMS messages: Three SMS messages were received, each claiming the device had entered China. This is a standard roaming notification from a cellular provider when a device is registered with a foreign network.
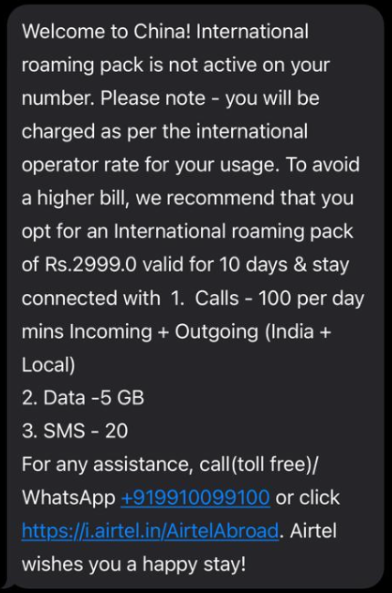
Fig.1 SMS message received by the high level Tibetan functionary
Initial Hypothesis
- Physical proximity to China
- Cellular provider error
- SIM Cloning/attack
- Cellular Network Attack
Detailed analysis:
Proximity to China: If the device user was near a Chinese border(e.g., Ladakh, Arunachal Pradesh, etc), their phone could have briefly connected to a Chinese cell tower or the person was actively traveling in China. This scenario was quickly ruled out after discussing it with the person who had not recently visited a border area.
Cellular Provider Error: While a system malfunction at the cellular network provider could theoretically trigger erroneous roaming messages, this was deemed unlikely. The generation of three such messages within a short time frame is improbable under normal error conditions. Welcome SMS are typically sent when a user’s home network detects a new registration event corresponding to the Mobile Country Code (MCC) and Mobile Network Code (MNC) of a roaming partner. In the case of a genuine network error, multiple users would typically be affected, not just a single device. However, only the victim’s phone received the Welcome SMS messages, with no indication of others experiencing similar roaming alerts. Furthermore, when the victim contacted the cellular provider, customer service stated they would escalate the issue to higher authorities. Had there been a system malfunction, the provider would likely have acknowledged the issue and notified the user. Since this did not occur, a provider-side error was ruled out.
SIM Cloning: SIM Cloning involves duplicating SIM card identifiers(IMSI, Ki) to intercept communications. The “Welcome to China” messages could indicate the cloned SIM registering on a Chinese network. However, SIM cloning is a static condition and would likely not result in intermittent network access or a user receiving a Welcome SMS message.
Cellular Network Attack: The victim symptoms stating they received multiple ”Welcome to China,” messages (likely a roaming Welcome SMS message), combined with signal loss and service interference indicates a manipulation of mobile network registration caused by manipulation of device network registration using either SS7 and DIAMETER, or traffic steering techniques.
How did the Cellular Network Attack occur?
IMSI number is essential for Cellular Network Attack because it serves as the primary identifier for a subscriber within a mobile network.
During our analysis of Cellular Network Attack and how the attacker might have got access to the IMSI number, we explored several attack vectors and the following scenarios:
- physical access to the device
- phone compromise
- Cellular Network Attack
During the investigation, we learned that the individual’s phone had never been accessed by a third party, as he was digitally savvy and adhered to security best practices. As such, we ruled out scenario A.
While investigating whether the phone was compromised, we performed a log analysis using MVT (Mobile Verification Toolkit) tools to detect any signs of a Pegasus attack.7 Additionally, we captured the phone’s network traffic with WireGuard and analyzed it, finding no evidence of a phishing attack, malicious traffic, or Pegasus infection. Therefore, we ruled our scenario B.
Through the process of elimination, only scenario C (Cellular Network Attack) was left for us to investigate more on. It is clear that the attackers were using a Cellular Network Attack using the IMSI number of the victim’s phone. In terms of the how the attackers were able to determine the IMSI, it could have been done through the following two methods:
- The attacking network identifies the location of a target IMSI (or IMSIs) using multiple possible techniques including a fake or portable base station (if outside of the attacker network footprint).
- Alternatively, a target user IMSI and country location can be acquired using other network procedures, such as through an IPX operator or by using an HLR query.
Possible Cellular Network Attack techniques used on target victims phone:
(1) Traditional Signaling Attack Using traditional 3G and 4G network vulnerabilities, an attacking network can fake and/or manipulate user registration, fork/split phone calls, redirect communication and deny service.
- Fake Registration - The attacker uses the target’s IMSI to send user authentication messages to intercept device authentication messages (for use in fake base stations) or registration messages to temporarily redirect communications.
- Eavesdropping - Using call forking signaling technique the attack could intercept or listen to a target’s communication, such as VoLTE phone calls.
- Denial of Service - A fake registration attempt can have the temporary effect of knocking the target user off the network or service degradation. Alternatively, a signaling application can use signaling to temporarily deny registration or repeatedly knock a device off of the network.
(2) Network Traffic Steering
This is an advanced technique used by attackers to manipulate Network Traffic Steering, aka Anti Steering of Routing (Anti-SoR), Seamless Capture of Roaming (SCAP). The attacker uses multiple Anti-SoR techniques to capture all, or a single network registration to force a user’s device to register onto an adversary network.
-
Steering Circumvention Technique – An attacking network application fakes the target user IMSI and sends repeated location update (registration) messages to force the target user’s home network operator to accept it. Typically, networks will allow a user to register to a non-preferred network after a certain number of attempts (this is network configurable parameter).
-
Kidnap Retention Technique (basic) – The attacking network will send fake location update messages from the user IMSI in response to the target user’s network sending a periodic cancel location message (this may happen based on different conditions), thus preventing the user from leaving the network.
-
Kidnap Retention Technique (advanced) – This advanced technique from the attacking network uses a combination of messages in succession designed to influence the target user’s network to retain a user’s registration on the attacking network.
Motive:
Various research studies have demonstrated/shown that the People’s Republic of China (PRC) targets Tibetan leaders with cyberattacks primarily for espionage purposes, aiming to monitor and disrupt political activities while undermining the operations of the Central Tibetan Administration (CTA) and Tibetan Civil society organizations. The CCP has the expertise and capabilities to carry out these sophisticated Cellular Network Attacks and can leverage its telecommunication companies to gain access to subscriber databases.
In this case, the victim is an influential high-level Tibetan functionary with a strong online presence and has contributed op-eds to various media outlets refuting PRC propaganda. The timing of this attack is also significant: recently, His Holiness the Dalai Lama published a memoir titled - Voice for the Voiceless,8 which has prompted a strong response from the PRC.
This sophisticated attack could be a deliberate scare tactic by the Chinese Communist Party (CCP) to intimidate Tibetan leaders in exile. The psychological impact of having personal or sensitive information exposed or fear of being monitored can discourage activism or public criticism of the CCP.
A more significant motive, however, could be the collection of network registration details—such as device identifiers like IMEI numbers, MAC addresses, or IP addresses—which would enable an attacker to track the physical location of a target’s device, monitor their movements, and identify their contacts. By intercepting or disrupting communications, the CCP could hinder coordination among exile leaders, undermine advocacy efforts, or obtain sensitive information. This tactic aligns with the CCP’s broader strategy of surveilling the Tibetan diaspora to map influence networks and suppress pro-Tibet activities.
Next Steps:
The TibCERT has been actively trying to determine how the attacker was able to determine the IMSI number whether it was through an IMSI catcher9 or using IPX operator10 and HLR query11 and will continue to reach out to relevant authorities to investigate it further. At the same time, we have been reaching out and will continue to raise this issue to Indian Cellular Network Operators to highlight the risk of this kind of manipulation and attack for Tibetans.
Recommendations:
If you think you are a victim of the Cellular Network Attack
- Change both phone and phone number:
If your device has been targeted through a Cellular Network Attack, such as SIM surveillance or network-level tracking, there is unfortunately very little you can do to fully protect yourself. In such cases, the most effective course of action is to completely disengage from the compromised hardware and number. This means purchasing a brand-new phone and subscribing to a new SIM card with a different phone number. It is critical that the new phone has never been used with your previous SIM card or connected to any services associated with your old number.
Importantly, changing just the phone or just the SIM card is not sufficient. Modern surveillance systems are capable of linking multiple identifiers such as your IMEI (device), IMSI (SIM), and past usage patterns. The goal is to reset all these identifiers in one go to disrupt any surveillance chain.
General recommendations to mitigate Cellular Network Attack
(Note: Following recommendations are for general protection of your phone, however with this kind of attack, the best solution is to keep your phone number private)
- Device Security
- Use smartphones with 4G/5G support, as these are harder to downgrade to 2G and disable 3G and 2G connectivity in device settings to prevent downgrade attacks.
- iPhone: You can do this by accessing the setting > Cellular > Voice & Data and choose 5G Auto
- Android: You can do this by accessing the setting > Connections > Mobile networks > Network mode and choose 5G only
- Use smartphones with 4G/5G support, as these are harder to downgrade to 2G and disable 3G and 2G connectivity in device settings to prevent downgrade attacks.
- Detection Tools
- Apps like SnoopSnitch12 (Android) can detect IMSI catcher activity by monitoring suspicious network behavior.
- Secure Your Phone Number with Your Carrier
- Enable Sim lock: Contact your mobile carrier and set up a unique PIN or passcode required for any account changes, like SIM swaps or porting. This is your first line of defense—make it strong (avoid birthdays or simple sequences like 1234).
- Minimize Exposure of Your Phone Number
- Avoid using mobile phones for sensitive discussion.
- Do not give away phone numbers: Many organizations still provide phone numbers on their visiting card as well as on the organizational website which increases exposure to the threats.
- Follow recommendation 9 for added security.
- Lockdown mode
- This is an advanced security feature designed to protect users from highly sophisticated cyber threats, such as spyware and state-sponsored hacking. Both iPhone and Android have implemented similar security measures to enhance digital safety.
- When your device is on lockdown mode, it offers counter advanced spyware measures to minimize attack surfaces.
- Update Software
- Keep your phone’s OS and apps updated to fixed vulnerabilities.
- Check for Suspicious Activity
- Watch for signs of cloning—sudden loss of signal, unexpected “SIM registered” texts, or unrecognized calls/texts on your bill. If your phone stops working abruptly, call your carrier immediately from another line.
- Use alternatives for 2FA
- Instead of SMS-based two-factor authentication, switch to app-based authenticators (e.g., Google Authenticator)13 or hardware keys (e.g., Feitian Titan Security key). SMS is vulnerable to interception and therefore we do not recommend it for two-factor authentication.
- Use Signal and share Signal ID
- Instead of sharing phone numbers, use Signal ID to enhance privacy and security.
- The cellular phone numbers use the Signaling System 7 (SS7) protocol which has significant security vulnerabilities with outdated design.
- By sharing Signal IDs, we can avoid exposing our phone numbers to untrusted parties, reducing the risk of SS7 attacks like SIM swaps or location tracking, thus enjoying secure communication.
Footnotes
-
An international mobile subscriber identity (IMSI) catcher, is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking location data of mobile phone users. ↩
-
An IPX (IP eXchange) operator is a company or entity that provides the infrastructure and services for interconnecting different telecommunication networks, including mobile and fixed operators, and other service providers, using IP-based protocols. ↩
-
Home Location Register (HLR) is a database of all active customers of a mobile network, including their number, service entitlement, and number porting history. ↩
-
International Mobile Subscriber Identity, IMSI, is a unique number automatically generated and stored in the SIM. It identifies every mobile phone subscriber on a UMTS or GSM network. ↩
-
SS7, or Signaling System 7, is a telecommunications protocol used to exchange information between network elements in public switched telephone networks (PSTNs) and mobile networks. ↩
-
Diameter is a next-generation industry-standard protocol used to exchange authentication, authorization, and accounting (AAA) information in Long-Term Evolution (LTE) and IP Multimedia Systems (IMS) networks. ↩
-
https://www.theguardian.com/news/2021/jul/18/what-is-pegasus-spyware-and-how-does-it-hack-phones ↩
-
https://www.amazon.in/VOICE-VOICELESS-Holiness-Dalai-Lama/dp/0008774099 ↩
-
An international mobile subscriber identity (IMSI) catcher, is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking location data of mobile phone users. ↩
-
An IPX (IP eXchange) operator is a company or entity that provides the infrastructure and services for interconnecting different telecommunication networks, including mobile and fixed operators, and other service providers, using IP-based protocols. ↩
-
Home Location Register (HLR) is a database of all active customers of a mobile network, including their number, service entitlement, and number porting history. ↩
-
https://play.google.com/store/apps/details?id=de.srlabs.snoopsnitch&hl=en_I ↩
-
https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2&hl=en_IN&pli=1 ↩


